Where 'House of Cards' gets tech wrong (pictures)
The second season of the hit Netflix series "House of Cards" incorporates lots of technology and hacker references, but do they ring true? Or more like Hollywood silliness? Caution: spoilers ahead!
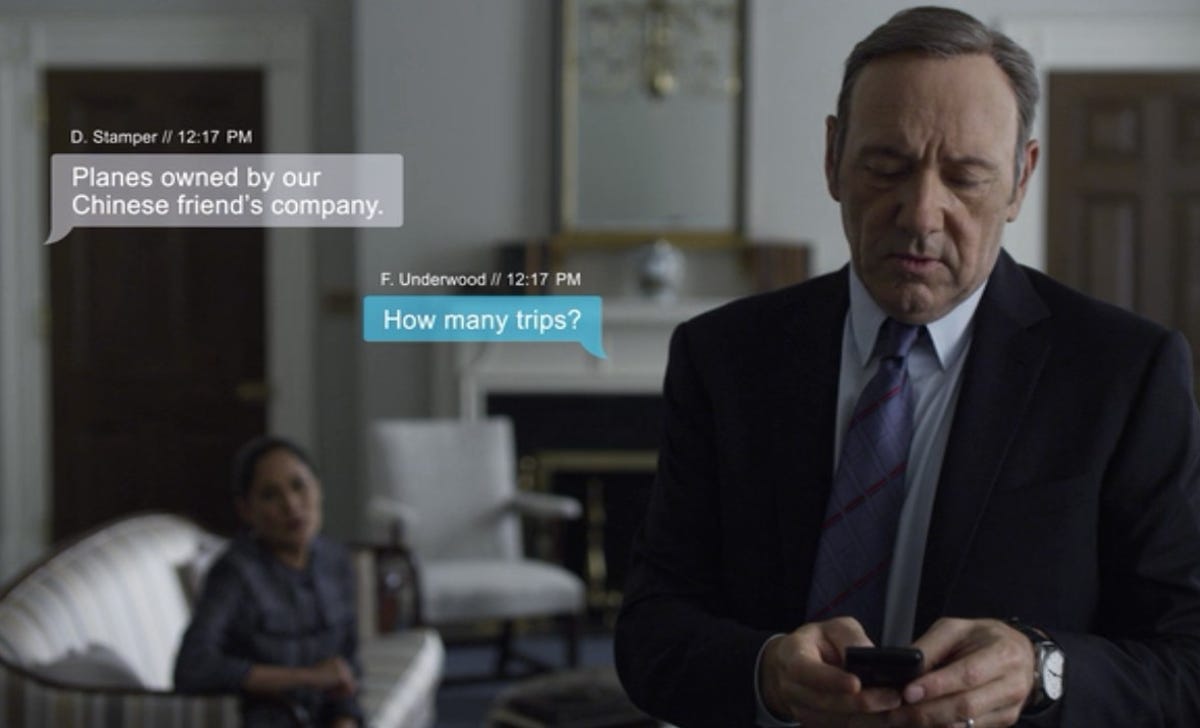
Faulty tech foundation
The hit Netflix series "House of Cards," starring Kevin Spacey, dropped all 13 episodes of its second season this month, leading to much binge streaming. While the political thriller is filled with enough drama, plot twists, and excellent performances to make an HBO exec twitch nervously, it has some rather odd ideas about how certain pieces of technology work. Sure, letting the audience in on Frank's text messages via onscreen graphics is a nice visual touch, and the show's treatment of technology is actually above-average for Hollywood, but there are still some loopholes and embellishments, plus a few knee-slappers, worth pointing out.
Caution, spoilers ahead! Stop here if you haven't finished watching the whole season.
This isn't Snapchat, sir
In the first episode of season 2, political heavyweight Frank Underwood tells journalist Zoe Barnes to delete her contact information for him, as well as their text exchanges, therefore eliminating all traces of their torrid relationship. Sure, except for all the other synced servers and devices those messages could be stored on, the phone company's records, and a little agency called the NSA. Frank must have iMessage and BBM confused with Snapchat, and even those messages don't completely disappear either.
What activation?
Doug Stamper hands his boss Frank Underwood a prepaid "burner phone" that looks an awful lot like a Trac Fone with the simple instructions to "just turn it on and dial." I guess this is sexier than the more likely prepaid process -- "just turn it on, dial into the activation number, spend a few minutes on hold, fumble around the package for the numbers the person at the call center would like you to validate, hang up, wait a few minutes, and then dial."
Password please
For some reason, the video footage of the D.C. subway sits behind a firewall on a police department server. We know this because one of the officers has to go through this screen to "log in" to the individual encrypted file... or something. It must be true because there are crazy fonts, red lines, and lock icons, right there in the dialog!
God of... NULL
In episode 2, the Secret Service disconnects Vice President Frank Underwood's video game console from the Internet because "it's not a secure connection." Really? The Secret Service can put blast-proof walls in the Underwood residence, but a virtual private network isn't possible? I set one up in about five minutes to watch the Olympics this month. I always knew I should have gone to work in D.C.
Deep Web or darknet?
At one point in episode 2, Lucas Goodwin gets a crash course in the "deep Web" from a colleague that's actually a pretty decent 30-second synopsis of what can be accessed using Tor. But the colleague also claims that this un-Googleable area makes up 96 percent of the Internet. Uh, that's a bit misleading. As Slate points out, this figure actually refers to anything that cannot be reached by crawling links, which would include any dynamically created pages, or anything behind a paywall, for example. In other words, anything without a permalink -- not exactly the dark recesses of the Web, which is more often and appropriately referred to as the "darknet."
Entering with a flourish
When the mysterious deep-Web hacker Gavin Orsay finally reaches out to journalist Lucas Goodwin, he does so with quite the dramatic flourish, apparently taking control of the video card on his laptop to great visual effect before splashing a series of pornographic images across the screen and finally landing on one of Zoe Barnes. This is followed by a nondescript chat window. Now, I'm sure there's someone out there who can tell me how all this could be done, but the bigger question is why? Why not just go straight to TorChat? It seems a cheap way to add an extra layer of "hackeriness" to Goodwin's little darknet liaison.
Bird brain
Hacker character Gavin Orsay's avatar, which he initially uses to communicate with Lucas Goodwin via a jailbroken iPad, is probably the bit of technology in "House of Cards" you're most likely to see mocked on social media. However, I find it's actually kind of a nice homage to hacker culture and a reference to a centuries-old painting in one, even if it's still a bit silly and excessive. 1990s hacker-turned-ex-con-turned-consultant Gregg Housh advised on season 2 and defends the scene, noting that it "is actually possible with a rooted tablet and some basic app-building skills."
Fingerprint FaceTime?
No, no, no, NO! Until episode 3 of the second season, "House of Cards" is above-average in its portrayal of tech, but when the anonymous hacker asks Lucas Goodwin to sign a "notary app" by putting his thumb over the iPad camera to take a fingerprint image, I nearly get whiplash shaking my head. Not only does it misunderstand the basic concept of notarizing a document, it confuses a fingerprint scanner with a, uh, camera. Put your finger over a camera and you prevent any visible light from hitting the lens. Ever take a photo in a pitch-black darkened closet? Of course you haven't, because you'd just get a black image, which is what would really happen here as well.
Where's the open source?
OK, I just have to nitpick something here. When our still-unseen hacker friend has his first voice conversation with Lucas Goodwin, he sends what seems to be a rooted iPad to him via courier. Really? The tablet of choice in the hacker underground is also the most expensive and least open? Where's the disposable Android tab? Or better yet, the roughed-together Ubuntu Touch prototype? I'm guessing the "House of Cards" production folks thought it more important for the audience to recognize that little Apple logo on the back.
Just swipe to unlock
Journalist Lucas Goodwin passes the hacker test by briefly stealing a phone that belongs to the Washington Herald IT guy to get through the two-step identification and help hacker Gavin Orsay gain access to the paper's servers. That's all fine, except Goodwin enjoys the unlikely advantage of dealing with the only IT guy in the world who doesn't password-protect his smartphone.
Dumb dongle hacking
And here is journalist Lucas Goodwin's undoing, where he's essentially entrapped into trying to break into AT&T's servers by physically slipping a dongle into one at the server farm. Of all the hacks we've heard about in recent years, I'm not aware of any that actually went down this way (that are public knowledge at least), with the possible exception of how Stuxnet was smuggled into Iran. Could an AT&T server farm actually be accessed this way? I don't know, but it seems like quite a stretch.
More importantly, while the ol' dongle-hack method makes sense in the case of a closed-off nation like Iran, wouldn't there be literally millions of easier ways (at least theoretically) to access and break into a massive, continent-wide telecom network? Of course, this could have been the point; Lucas was getting played, after all, and he didn't really seem to perform his journalistic due-diligence on server security before agreeing to try to break into one.
So, the lesson here is that all lazy journalists get hauled off to jail. Now, if you'll excuse me, there are two men with suits and badges at my door. Uh-oh.

