Google keeps an ever-closer eye on non-Play Store apps
Google is taking additional steps with Verify Apps to protect Android users from potentially malicious non-Play Store apps, even after they've been installed.
SAN FRANCISCO -- Android owners who use apps installed from outside of the Play Store will soon find their devices just a smidge safer, as Google announced at the RSA Conference here that Verify Apps will soon keep an eye on non-Play Store apps even after you install them.
Adrian Ludwig, Google's Android security engineer lead, said the change builds on the Verify Apps security feature introduced last year. He explained the change during a talk on how Google has created a secure open-source operating system.
When the Verify Apps option is checked, Google will scan apps installed outside of the Play Store to make sure they're not malicious. This was a one-time check, but the new component, which requires no additional changes by the user, will warn you when an app is determined to be malicious even if it passes muster the first time around.
Users will see a warning in the notification tray, so the ultimate decision to leave a suspected malicious app on the device remains up to the user. Google said the feature is rolling out in the coming weeks.
Ludwig mentioned the Verify Apps improvement while discussing Android's layered security protocol, which creates multiple levels of security including app sandboxing, permissions, additional security provided by third-party apps, and Android's basis on SELinux itself.
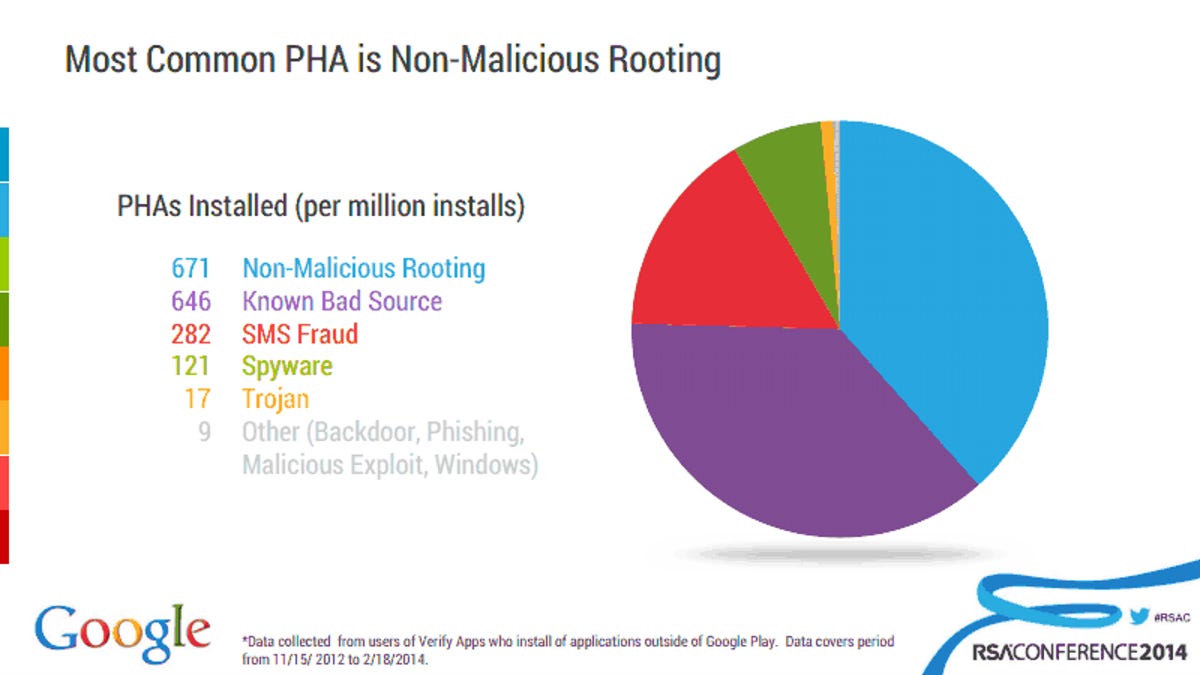
He also revealed some Android security facts indicating that the rate of infection from Potentially Harmful Apps is low.
100 percent of devices have sandboxes and permissions; 95 percent of devices have Verify Apps; Most devices only install from trusted sources; Around 0.8 percent of app installs from unknown sources receive a warning; Less than 0.18 percent of apps from unknown sources are installed after a warning; Less than 0.001 percent of installed apps attempt to evade runtime defenses; Google doesn't know what percentage of installed apps evade runtime defenses and cause harm, but it's less than 0.001 percent of apps.
Ludwig also presented a case study on Android malware. In the case of the "Master Key" vulnerability discovered last year, Google revealed more facts:
There's no evidence of exploits before the flaw was revealed at the Black Hat conference; One day after Google was notified, Google Play was secured; Less than one month after Google was notified of the Master Key problem, the patch was delivered to Open Handset Alliance partners; One month after Google was notified, the company verified that apps had been secured; One month before the first exploit was reported, devices began to receive updates; Installs exploiting Master Key from unknown sources: less than 8 in 1 million; Estimated installs that exploited the Master Key flaw: less than 1 in 1 million.

