Microsoft advising users to apply latest critical security patches
Windows users are being asked to install the latest round of Microsoft's Patch Tuesday updates to fix a range of critical bugs in key software.
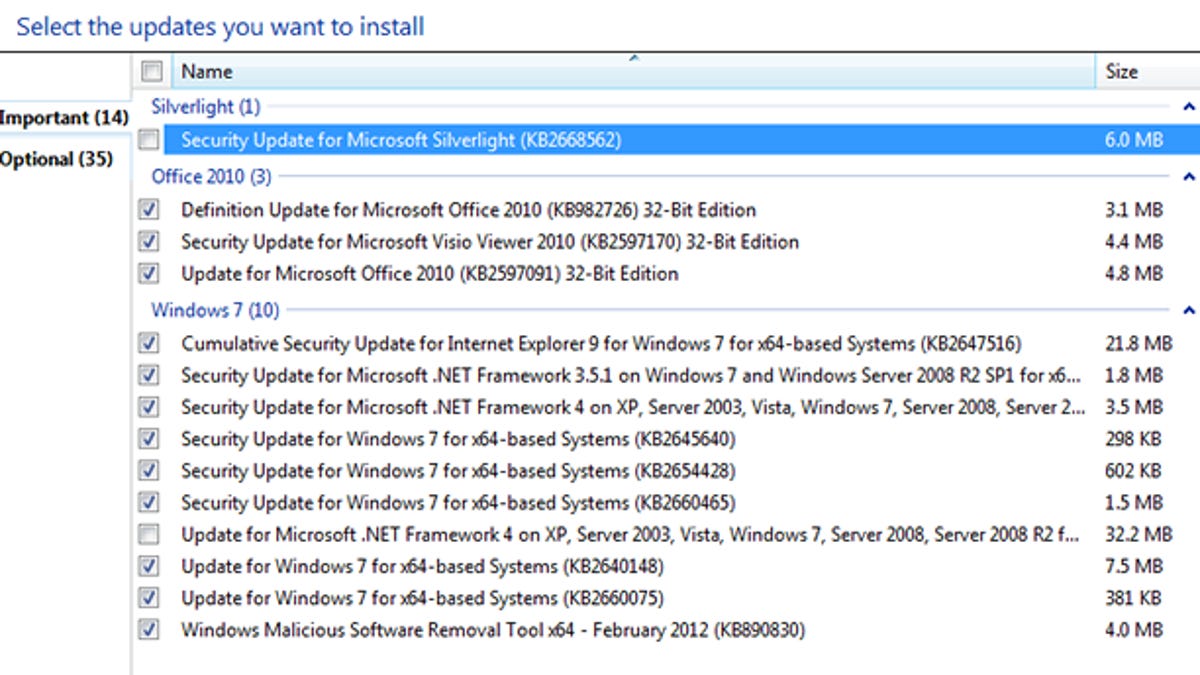
Microsoft is urging Windows users to apply yesterday's security updates to patch critical holes affecting Internet Explorer and Media Player.
The critical IE update affects versions 7, 8, and 9, and could allow an attacker to remotely run code on a user's PC using a "specially crafted Web page," according to Microsoft. As such, someone who exploited the hole could grab the same rights as the local user, of special concern if the user has administrative rights.
The update brings Internet Explorer 9 up to version 9.0.5. The vulnerability also affects IE 6 but is rated just moderate for the older browser.
People with automatic updating turned on will see the updates installed by default. Other users will have to manually trigger them.
"Most customers have enabled automatic updating and do not need to take any action," Microsoft said in its IE blog. "We recommend that customers, who have not enabled automatic updating, enable it (Start Menu, type "Windows Update"). We recommend that administrators, enterprise installations, and end users who want to install this security update manually, apply the update immediately using update management software or by checking for updates using the Microsoft Update service."
One of the updates specifically patches a hole in a Microsoft C Run-Time Library DLL file (msvcrt.dll), a file that comes with Windows.
Attackers able to take advantage of the vulnerability could create a hazardous Web page or file that launches Windows Media Player, thus triggering a payload of malware.
Though msvcrt.dll is a common DLL used by many applications, Microsoft said that Media Player is the only component so far known to be vulnerable.
Still, the patch will protect any other potentially at-risk applications should they be discovered. And beyond Microsoft's own software, other third-party programs tap into this file, so applying the patch will secure them as well.
New vulnerabilities are discovered all the time, the price we pay for using certain software. But Windows users can protect themselves by following the usual advice: installing the latest patches, ensuring that your security software is up to date, and enabling UAC (user access control). No method guarantees absolute security, but adopting as many of these defenses as possible is still your best bet.

