Data theft attacks besiege oil industry, McAfee says
Industrial espionage appears to be the motivation for successful, long-running attempts to obtain confidential data from oil and energy companies, the security firm says.
For years, companies in the oil and energy industry have been the victims of attempts to steal e-mail and other sensitive information from hackers believed to be in China, according to a new report from McAfee.
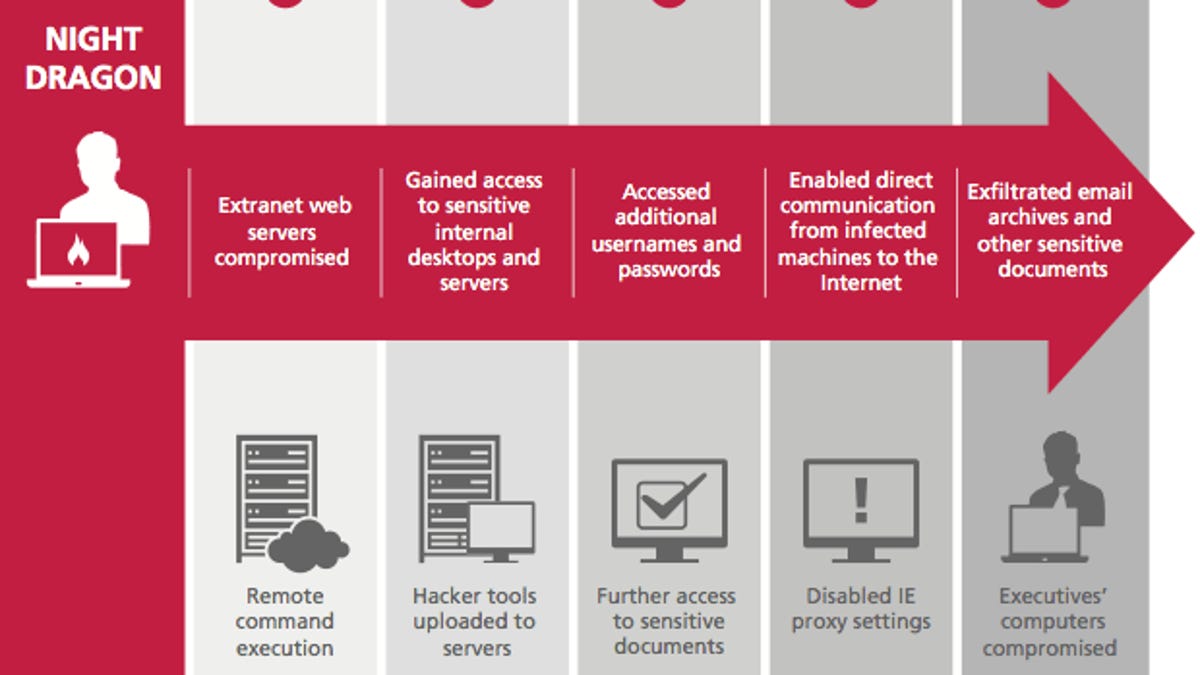
The attacks, to which McAfee gave the sinister name "Night Dragon," penetrated company networks through Web servers, compromised desktop computers, bypassed safeguards by misusing administrative credentials, and used remote administration tools to obtain the information, the security firm said late yesterday. McAfee and other security companies now have identified the method and can provide a defense.
"Well-coordinated, targeted attacks such as Night Dragon, orchestrated by a growing group of malicious attackers committed to their targets, are rapidly on the rise. These targets have now moved beyond the defense industrial base, government, and military computers to include global corporate and commercial targets," McAfee said in a white paper (PDF) published today.
And the attack was at least partially successful, McAfee said: "Files of interest focused on operational oil and gas field production systems and financial documents related to field exploration and bidding that were later copied from the compromised hosts or via extranet servers. In some cases, the files were copied to and downloaded from company Web servers by the attackers. In certain cases, the attackers collected data from SCADA systems," the supervisory control and data acquisition systems that control and monitor industrial processes.
McAfee didn't reveal details about what SCADA data was involved, but it's a potentially serious matter: such systems are at the operational heart of everything from oil pipelines and refineries to factories and electrical power distribution networks.
McAfee told The Wall Street Journal that the attacks appeared to be purely about espionage, not sabotage. The latter possibility has become a more vivid fear with the Stuxnet attack that apparently damaged Iranian nuclear operations. China is a particular concern: it's a rising industrial power that Google has implicated in attempts to crack its own network and obtain sensitive information.
McAfee notified the FBI of the Night Dragon attacks, and the FBI is investigating, the Journal reported.
Several Night Dragon attacks were launched in November 2009, McAfee Chief Technology Officer George Kurtz said in a blog post, but attacks have been going on for at least two years and likely as long as four.
"We have strong evidence suggesting that the attackers were based in China," Kurtz said. "The tools, techniques, and network activities used in these attacks originate primarily in China. These tools are widely available on the Chinese Web forums and tend to be used extensively by Chinese hacker groups."
The attacks themselves used a variety of methods that, although described as "relatively unsophisticated," were nonetheless effective.
First came an attack to compromise a Web server that then became a host for a variety of hacking tools that could probe the company's internal network. Password cracking and other tools were used to gain access to PCs and servers. Remote administration software, including one called zwShell, let attackers control compromised Windows PCs to gather more data and push the attack toward more sensitive areas.
An appendix of the white paper offers more details on the Chinese connection:
While we believe many actors have participated in these attacks, we have been able to identify one individual who has provided the crucial C&C infrastructure to the attackers--this individual is based in Heze City, Shandong Province, China. Although we don't believe this individual is the mastermind behind these attacks, it is likely this person is aware or has information that can help identify at least some of the individuals, groups, or organizations responsible for these intrusions.
The individual runs a company that, according to the company's advertisements, provides "Hosted Servers in the U.S. with no records kept" for as little as 68 RMB (US$10) per year for 100 MB of space. The company's U.S.-based leased servers have been used to host the zwShell C&C [command and control] application that controlled machines across the victim companies.
Beyond the connection to the hosting services reseller operation, there is other evidence indicating that the attackers were of Chinese origin. Beyond the curious use of the "zw.china" password that unlocks the operation of the zwShell C&C Trojan, McAfee has determined that all of the identified data exfiltration activity occurred from Beijing-based IP [Internet Protocol] addresses and operated inside the victim companies weekdays from 9:00 a.m. to 5:00 p.m. Beijing time, which also suggests that the involved individuals were "company men" working on a regular job, rather than freelance or unprofessional hackers. In addition, the attackers employed hacking tools of Chinese origin and that are prevalent on Chinese underground hacking forums. These included Hookmsgina and WinlogonHack, tools that intercept Windows logon requests and hijack usernames and passwords...
Although it is possible that all of these indicators are an elaborate red-herring operation designed to pin the blame for the attacks on Chinese hackers, we believe this to be highly unlikely. Further, it is unclear who would have the motivation to go to these extraordinary lengths to place the blame for these attacks on someone else.

