Alright I am recording.
[MUSIC]
So my name is Irfan Asrar, and thank you for having me.
I'm with Blue Hexagon>> This application shadow that was developed by acronym, released invested in by acronym has suddenly become the hottest app in the world for
[LAUGH]
Very Challenging reasons.
Right..
And a copy of the application.
How did you obtain this application.
Once a year [INAUDIBLE] and somebody who's specialized in targetted attacks and dealing with situations where you've got journalists who were targetted.
We have an anonymous drop off with people submit apps
Applications or emails or something that they feel may be tied to a targeted ad campaign, but we didn't actually have to put any of that effort into getting this app.
This app appeared in our collection yesterday and literally at the same time we got it, we started looking at where it had originated from.
It originated from a source called [INAUDIBLE] Total, which is widely used across the industry across the globe as a source for samples, so this app was uploaded there and eventually it went Everywhere, you know, into the collection, drop boxes of every security company around the globe.
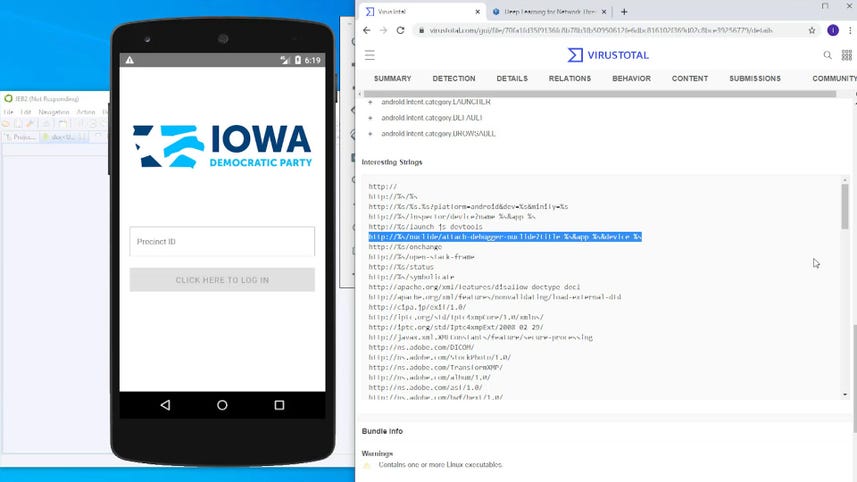
So essentially what you're seeing in front of you is basically some of the information of site called virus total where it was uploaded to what you're seeing there is information related to the text that was using the app.
Basically paragraphs of text as well as url and links.
Contained in the app.
And what you're seeing here is a couple of examples of URLs that basically shouldn't have probably not been in there.
There's actually a link to somebody's personal website in here.
We believe this is the final release version of the app, not an app that was in testing before the actual caucus.
We believe this is the app is actually distributed independently to all the people military and to the precinct leaders.
Off to us.
What would information like a personal website or that other scruff state in an application that is live and being used in the wild?>> That's a very good question.
We're hoping Sharon corporate can set some shed some light on that.
But what we believe is this is an oversight and this is kind of an example of the app being rushed into production.
So,a couple of overarching concerns is the fact that we were able to obtain the app so easily without literally no effort.
That means other people can including access to information about infrastructure supporting this app, which basically gives us a target attack surface to focus on if we wanted to cause disruption.
Can you explain how precisely did this app fail?
Well, I'll so we're some kinda getting some details on that we believe that there may be some issues in the back end which is not exposed here in the code.
But what we believe should have taken place was the device should have been provided By the Iowa with Democratic Party, a lockdown device that would not allow the app the user to deviate from the functioning of the FDA or any other app.
That way you have the integrity of the device verified, make sure that the device has not been tampered with before before it installs.
The other thing is because the Android platform is so fragmented it's really hard to get it out the function across all devices.
That is one reason, [UNKNOWN]
There were reports that this app also had problems communicating with the server back home So, I'm from Iowa and I know how [UNKNOWN] can get especially if you're away from cell phone transmitters or several miles from a cell phone transmitter and you have maybe a weak signal
You're in a crowded gym with a lot of other people with phones trying to talk to the internet.
So, what in terms of you know, given that environment, should developers have done not just I understand lock down a production device, but what could they have done given?
They knew what Iowa was like and the the degree to which cell connectivity was available.
What that's a great question.
And you know, it's really hard especially if you go into rural provinces or regions.
Where communication may not exactly have the same kind of infrastructures you have and cities.
They should have tested that framework.
They should have tested the environment for all possibilities.
They should have Accounted for areas where signal strengths would not be as strong as they are in other regions.
And they should have basically found a way for the data not to attempt to transmit, or be held back and transmitted at a later time.
We know that Nevada was planning to use this for their caucus.
We know that Texas had probably use this for a lot of the text messaging campaigns.
And we know that some of the candidates were invested in the application.
First of all, do you know what states were planning to use this app?
And what candidates were planning to use this app?
No, unfortunately not.
We're still in the process of trying to obtain that information.
But we still haven't able to lock down what exactly is the prevalence and the usage.
And the So this is going to be a protracted campaign.
Through the general election.
The primaries are already really hot.
Even for states who haven't planned to use this app, almost every state is planning to use technology of some sort going forward.
What should states What should people do?
What should voters do?
What should we be prepared for going forward?
Now then that's a really good question.
And you know, one of the things first of all, you know, full disclosure, I'm not a Democrat or Republican.
I'm actually Canadian.
I don't have an axe to grind against anybody involved here.
But one of the things that has plagued the US in terms of model elections and the use of electronic devices to facilitate and gather information is cyber security in the election processes.
It's traditionally been week a couple years ago, you could actually.
In fact, last last month we acquired several devices from PBA.
Religion, the election voting system that we use in previous years.
And you can see that those devices can be easily sync so this was not a surprise.
It was a really scary wake up call.
What I think they should be doing is approaching security consultants.
To get basically independent screening of the app, look at the processes involved and the weak points and identify the attack surface before they go forward.
Last question, what didn't I ask that I really should have asked you You know what?
That's a good question.
I think the fact that now that you've got this app available globally, I think the concern is who else is looking at this app?
And what are the intent behind them looking at the app?
And that's what my biggest concern if these app, see the infrastructure that is associated to this attack today, we can definitely point to the fact that the information exposed the code that you are seeing Was probably one way they had access to information on what sites to target.