Microsoft, Symantec shutter another botnet
Symantec and Microsoft join forces to stop a botnet, and for the first time they provide clean-up tools directly to people with infected computers.
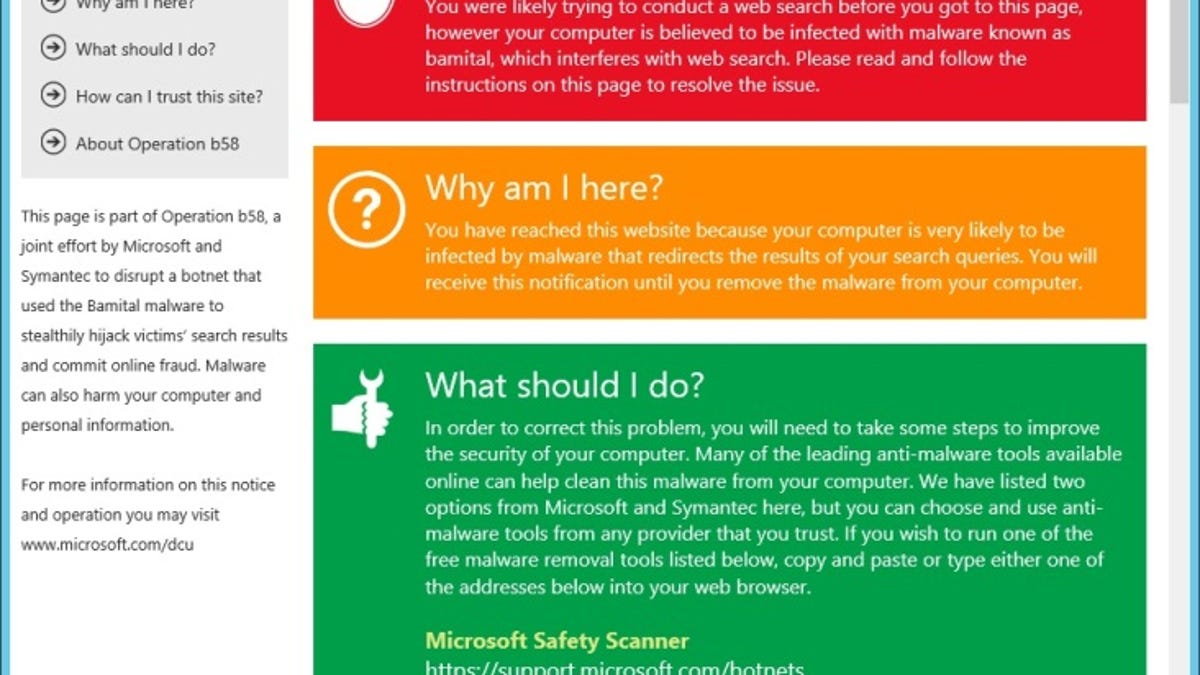
Microsoft and security software maker Symantec have revealed that they collaborated on the take-down of a botnet that had infected hundreds of thousands of computers.
By stopping the botnet, infected computers were reportedly unable to search the Internet. According to the story as first reported by Reuters, this is the first time that the companies which stopped the botnet directly warned people who had infected computers and offered them clean-up tools.
The botnet, called Bamital, is the sixth one that that Microsoft has received a court order to stop since 2010 and the second that it has worked with Symantec to halt. Last week, the companies asked for a court approval to shut it down, reported Reuters.
Vikram Thakur, principal security response manager at Symantec, explained the scope of the infections in a joint phone call with Microsoft's assistant general counsel to its Digital Crimes Unit, Richard Boscovich. "The data we have shows that the infections were extremely global, with the largest number of users in the United States," Thakur said.
Read the Microsoft legal filing against the 18 parties accused of running Bamital.
Bamital worked by redirecting sites you would click on in search results from Google, Bing, and Yahoo to Web sites controlled by the parties responsible for the botnet. Bamital would "subvert legitimate results," said Jeff Williams, currently director of the Security Strategy unit for Dell SecureWorks. Last year Williams worked directly on the Bamital botnet case for Microsoft's Digital Crimes Unit. "This is different from a toolbar [like Ask or Conduit] which isn't taking over specific search results," he told CNET.
In the case of the Bamital botnet, which Reuters said earned at least $1 million per year, Symantec had approached Microsoft more than a year ago to collaborate on stopping it. Thakur said that although this botnet was only a medium-size one, with 300,000 to 600,000 infected computers, it was not easy to stop.
"When we started following the botnet a year ago, it went through several iterations over the year's time. For us to gather all the evidence, to understand how to put a plan together to spare users from negative effects after it went down, it took about a year," he said.
Microsoft's Boscovich added that this kind of iteration is unusual for a botnet. "The interesting thing about this is that the people behind the botnet were playing with the botnet over time, fine-tuning the botnet, so it took some time until it was stable enough for us to make our move," he said.
Williams said that one aspect of the Bamital case is that the "criminals" will "move the botnet servers from one location to another to another. The trade craft of criminals is constantly evolving, so as the techniques of law enforcement get better, the criminals will change their tactics over time.
Boscovich and Thakur agreed that while you can expect more botnets going forward, improving laws and further collaboration between companies like Microsoft and Symantec will make it harder for the botnet to succeed.
"The more we do these operations, the more it becomes evident in the underground community that we're onto them," Boscovich said. The collaboration between Microsoft and Symantec, as well as the particular way that the Bamital botnet was structured, allowed the two companies to do more than just shutter the botnet and warn Internet service providers.
Thakur said that this is the the first time in a botnet case that the groups responsible for stopping it were able to provide a warning site and tools to disinfect afflicted machines.
"We wanted to make sure that when the victim would search, they would see a page that looked like a legitimate Microsoft page, with Microsoft and Symantec's logos. It would explain in clear language why they were there and how to clean their computer," said Boscovich. "It was also specific about saying that they could go to the AV [antivirus] provider of their choice. But we also made it clear that if they did, their computer wouldn't be cleaned."
Williams noted that Netherlands' National High Tech Crime Unit provided a warning page in the 2010 take-down of the Bredolab botnet, but did not offer malware removal tools.
In addition to directly helping people whose computers were infected, Microsoft took the unusual step of including aliases, e-mail addresses, physical addresses, and telephone numbers of those accused of running the botnet.
Although the botnet was run by 18 "ringleaders" scattered across the world, investigators at Microsoft's Digital Crimes Unit told Reuters that the botnet was most likely Russian in origin thanks to the inclusion of a Russian phrase in one of the botnet's cookies.

