Klocwork: Our source code analyzer caught Apple's 'gotofail' bug
If Apple had used a third-party source code analyzer on its encryption library, it could have avoided the "gotofail" bug.
It was a single repeated line of code -- "goto fail" -- that left millions of Apple users vulnerable to Internet attacks until the company finally fixed it Tuesday.
That OS X security vulnerability, which also affected iOS users, arose out of Apple's custom implementation of a security standard known as SSL/TLS. By including the "goto fail" line twice in a row, the normal error check for some types of encryption signatures fails.
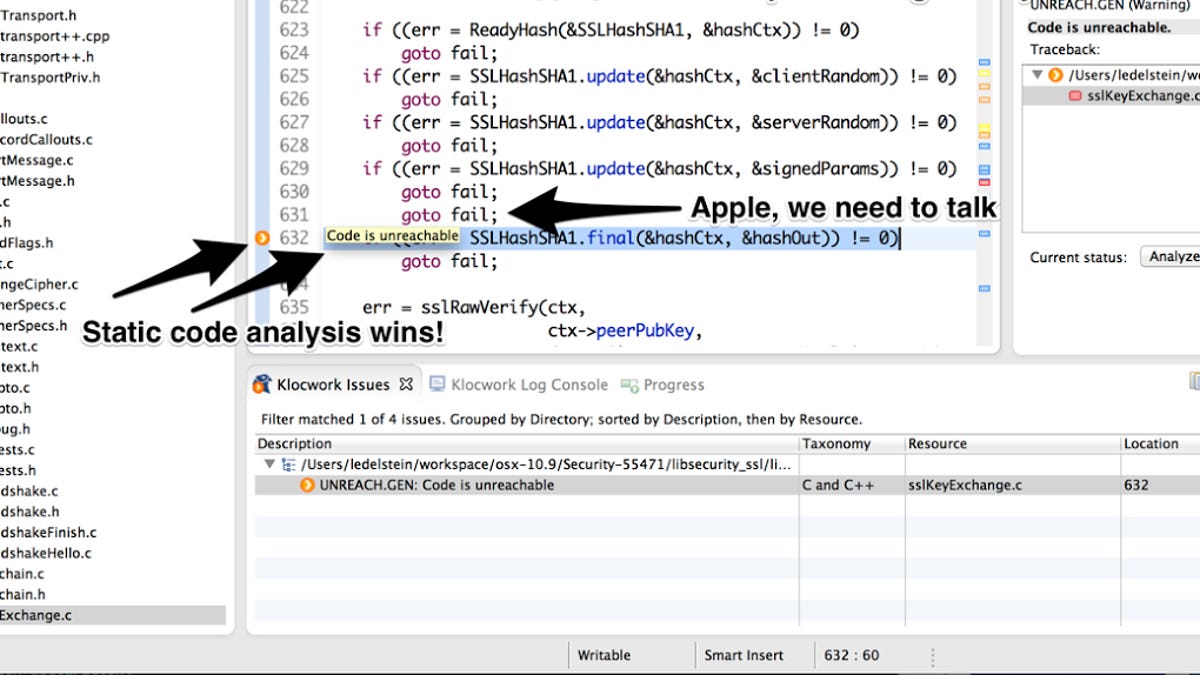
Now Klocwork, a company that makes source code analysis tools, is demonstrating that its product would have caught the errant second "goto fail" line -- if only Apple had been using it.
"It's like an automated code review," said Larry Edelstein, a sales engineer with Klocwork, which is owned by Rogue Wave Software. "The best SCA products, like ours, offer powerful inter-procedural analysis that can spot those issues, which arise only when sections of code from several disparate locations get tied together in a single control flow."
Edelstein sent CNET a screen snapshot showing that Klocwork's analysis tool flagged line 632 and the "goto fail" bug with an error message saying: "Code is unreachable."
This was not merely a hypothetical security hole. Aldo Cortesi, a New Zealand security consultant, posted a version of the mitmproxy utility that gives access to encrypted traffic when, he said, the computer is using "Apple's broken implementation" of SSL/TLS. Cortesi added: "It's difficult to overstate the seriousness of this issue. With a tool like mitmproxy in the right position, an attacker can intercept, view, and modify nearly all sensitive traffic."
And, of course, there's been plenty of speculation that the National Security Agency or other spy agencies would have exploited the bug. (If nothing else, they have the budget to purchase a license to Klocwork or similar products and test Apple's encryption code, which is publicly posted.)
Apple did not respond to questions for this article.

