Global cyber-espionage operation uncovered
Operation Shady RAT--unearthed by McAfee and deemed "historically unprecedented"--has stolen information from scores of public and private organizations in 14 countries.
A widespread cyber-espionage campaign stole government secrets, sensitive corporate documents, and other intellectual property for five years from more than 70 public and private organizations in 14 countries, according to the McAfee researcher who uncovered the effort.
The campaign, dubbed "Operation Shady RAT" (RAT stands for "remote access tool") was discovered by Dmitri Alperovitch, vice president of threat research at the cyber-security firm McAfee. Vanity Fair's Michael Joseph Gross was first to write about the findings. The targets cut across industries, including government, defense, energy, electronics, media, real estate, agriculture, and construction. The governments hit include the U.S., Canada, South Korea, Vietnam, Taiwan, and India.
While most of the targets have removed the malware, the operation continues, according to McAfee. The company learned of the campaign in March while investigating a command-and-control operation it had discovered in 2009, but traced the activity back to 2006, Alperovitch said in a conference call. McAfee was able to gain control of the command-and-control server and monitor the activity.
Alperovitch said he had briefed senior White House officials, government agencies in the U.S. and other countries, and U.S. congressional staff. He also has notified the victims and is working with U.S. law enforcement agencies on the investigation, including shutting down the command-and-control server.
"We actually know of hundreds if not thousands of these servers also used by this actor," he said in the conference call. "The entire economy is impacted by these intrusions. Every sector of the economy is effectively owned persistently and intellectual property is going out the door...It will have an impact on our jobs, the competitiveness of our industries, and on our overall economy."
Related stories:
• China linked to new breaches tied to RSA
• U.S. military wants to 'protect' key civilian networks
• Researchers warn of SCADA equipment discoverable via Google
Typically, a target would get compromised when an employee with necessary access to information received a targeted spear-phishing e-mail containing an exploit that would trigger a download of the implant malware when opened on an unpatched system. The malware would execute and initiate a backdoor communication channel to the command-and-control server, Alperovitch wrote in the report, which was posted to the McAfee blog.
"This would be followed by live intruders jumping on to the infected machine and proceeding to quickly escalate privileges and move laterally within the organization to establish new persistent footholds via additional compromised machines running implant malware, as well as targeting for quick exfiltration the key data they came for," Alperovitch wrote.
"Having investigated intrusions such as Operation Aurora [which targeted Google and others] and Night Dragon (systemic long-term compromise of Western oil and gas industry), as well as numerous others that have not been disclosed publicly, I am convinced that every company in every conceivable industry with significant size and valuable intellectual property and trade secrets has been compromised (or will be shortly), with the great majority of the victims rarely discovering the intrusion or its impact," Alperovitch wrote. "In fact, I divide the entire set of Fortune Global 2000 firms into two categories: those that know they've been compromised and those that don't yet know."
Unlike recent denial-of-service attacks and data breaches from groups like Anonymous and LulzSec (see chart of recent attacks), these espionage cases are more persistent, insidious, and threatening, and they cause much more harm, revealing important research and development information that can help countries better compete in markets, according to Alperovitch.
"What we have witnessed over the past five to six years has been nothing short of a historically unprecedented transfer of wealth -- closely guarded national secrets (including from classified government networks), source code, bug databases, email archives, negotiation plans and exploration details for new oil and gas field auctions, document stores, legal contracts, SCADA configurations, design schematics and much more has 'fallen off the truck' of numerous, mostly Western companies and disappeared in the ever-growing electronic archives of dogged adversaries," he wrote.
"What is happening to all this data -- by now reaching petabytes as a whole -- is still largely an open question," he continued. "However, if even a fraction of it is used to build better competing products or beat a competitor at a key negotiation (due to having stolen the other team's playbook), the loss represents a massive economic threat not just to individual companies and industries but to entire countries that face the prospect of decreased economic growth in a suddenly more competitive landscape and the loss of jobs in industries that lose out to unscrupulous competitors in another part of the world, not to mention the national security impact of the loss of sensitive intelligence or defense information."
It's unclear exactly who is behind the operation, but Alperovitch believes it is state-sponsored, although he declined to speculate which country might be responsible.
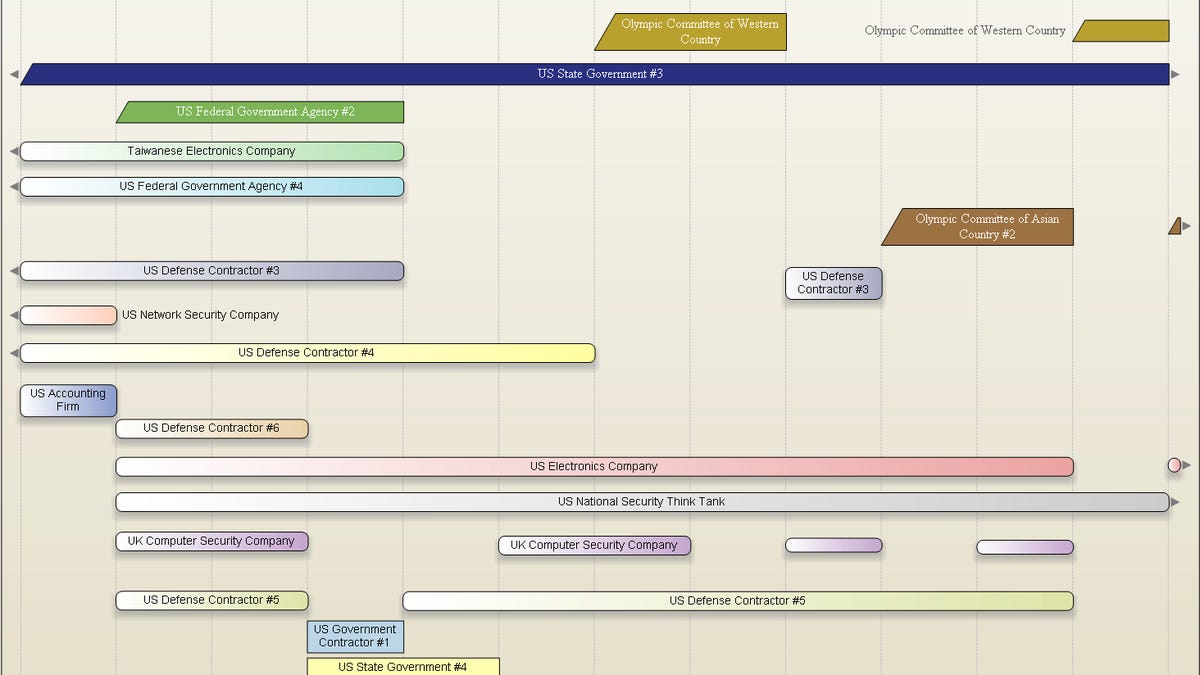
An educated guess might be China, given the targets. They include organizations in the U.S., most countries in Southeast Asia, but none in China, and many defense contractors. Also attacked were the United Nations, the World Anti-doping Agency, and the International Olympic Committee and Olympic committees in three countries, which were targeted right before and after the 2008 Olympic Games in Beijing, according to the report. China has disputed allegations that it has engaged in cyber espionage or attacks in the past.
"The presence of political non-profits, such as the private western organization focused on promotion of democracy around the globe or U.S. national security think tank is also quite illuminating," Alperovitch wrote.
The report has a chart that lists all 72 targets; most are not named but are listed by type and country or location, along with country of origin, start date of the initial compromise, and duration of the intrusions. There is also a fascinating timeline that shows each intrusion and its duration by year.
Espionage goes on all the time, but it's not often that details surface publicly. Several weeks ago security firm Invincea disclosed information about a spear-phishing campaign that was targeting the U.S. defense industry. In that case the e-mail purported to come from the U.S. Intelligence Advanced Research Projects Activity (IARPA) and used an Excel spreadsheet with defense contacts as bait, Invincea Chief Executive Anup Ghosh said in an interview today. More details are on the Invincea blog..
Researchers have to be careful in disclosing information about foreign cyber-espionage campaigns so they don't compromise surveillance and investigations the U.S. government might be conducting related to those operations, Ghosh said.
"We couldn't tie the operation to a nation-state, like McAfee did," he said.
Updated August 3 at 6:30 a.m. PT with details from the McAfee report, at 9:58 a.m. PT with details from a conference call, and at 11:56 a.m. PT to clarify timing of McAfee investigation and include Invincea disclosing espionage campaign.