Zero-day Windows kernel bug used in Duqu infections
Microsoft says it is working on a security patch to close a hole being used by the Trojan to infect systems.
Researchers have figured out one way the Stuxnet-like Duqu Trojan is infecting computers--via a Word document that exploits a previously unknown Windows kernel bug.
The installer file is a Microsoft Word document that exploits the kernel vulnerabilty, which allows code to be executed on the infected system, Symantec said in a post on its site. There may be other infection methods used by other Duqu variants that have not been uncovered yet, Kevin Haley, a director with Symantec Security Response, told CNET.
Microsoft is working on a fix, according to Jerry Bryant, group manager for response communications at Microsoft Trustworthy Computing.
"Microsoft is collaborating with our partners to provide protections for a vulnerability used in targeted attempts to infect computers with the Duqu malware," he said in a statement. "We are working diligently to address this issue and will release a security update for customers through our security bulletin process."
Most antivirus vendors detect and block the main Duqu files, but until a Microsoft patch is out companies should avoid opening documents from unknown parties, Symantec said.
Hungarian security lab CrySyS, which discovered Duqu initially, wrote in a post on its Web site that it had finally figured out how Duqu was infecting computers. Symantec researchers confirmed it and contacted Microsoft.
The Word document containing the Duqu installer was created to target a specific organization and to only install during an eight-day window in August, Symantec said.
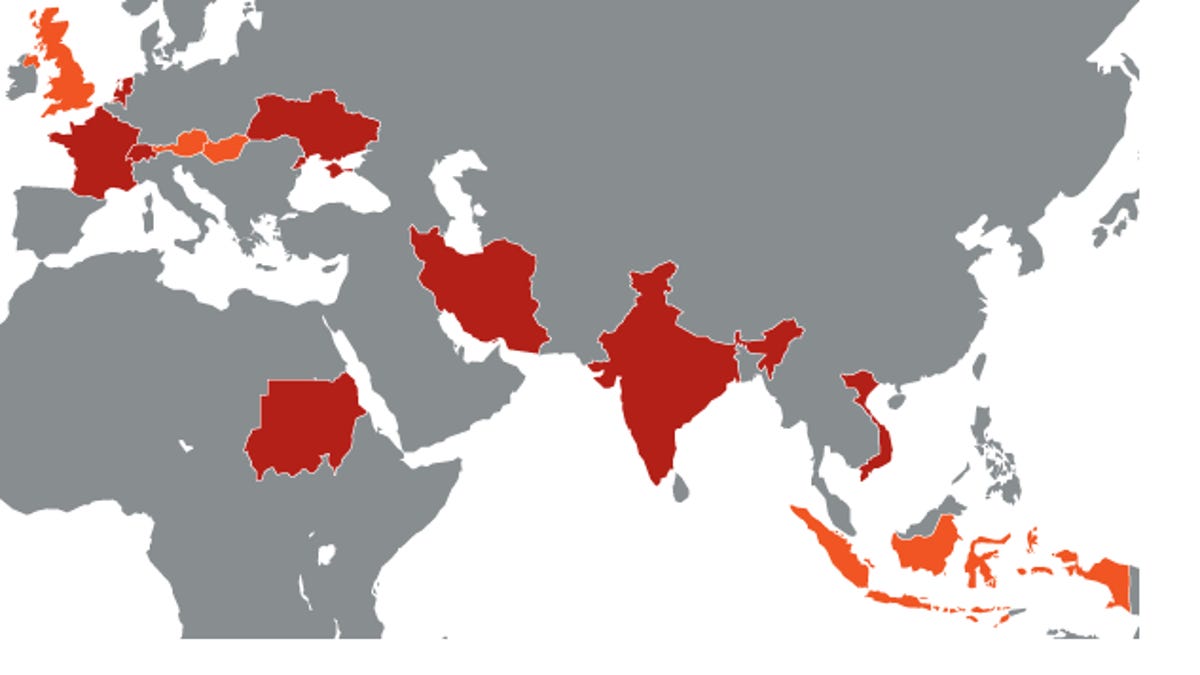
It's unclear how widespread Duqu is. Symantec has traced infections within six organizations in eight countries: France, Netherlands, Switzerland, Ukraine, India, Iran, Sudan and Vietnam, according to Symantec. Other security vendors have reported infections in Austria, Hungary, Indonesia and the United Kingdom, as well. Symantec declined to identify what organizations were found to have infections and said that in some instances the infection was traced to an Internet Service Provider and the original infection from there is unknown.
Once it gets inside an organization it can spread to other computers by copying itself to shared network drives and can even reach computers that aren't connected directly to the Internet via a peer-to-peer network within the organization, Haley said.
Researchers also have discovered that in addition to infected computers communicating with a command-and-control server in India, a server in Belgium had been used, he said.
"We continue to believe this is all about reconnaissance, collecting information," Haley said. "The first mystery--how did it get on machines?--has been solved, at least in one method. We still don't know how they were going to use that information" or who is behind it, he added.
Symantec went public with the information two weeks ago, suggesting that Duqu could be a precursor to another sophisticated attack like Stuxnet, which was the first to specifically target critical infrastructure organizations.
While Symantec says Duqu is similar to Stuxnet, they appear to target different systems and do different things. Stuxnet, which also infected targets via several zero-day Windows holes as well as USB drives, targeted specific Siemens supervisory control and data acquisition (SCADA) software and modified programmable logic controllers used in industrial control environments. It is believed to have been designed to sabotage Iran's nuclear program. Duqu, meanwhile, was found in a variety of organizations, including suppliers to industrial facilities, and steals data, like design documents, but does not appear to interfere with any operations, Symantec says.
"The payloads and other parts are new" in Duqu, Haley said. But "we stand by our analysis of the threat that parts were built off the original Stuxnet source code."

