Symantec uncovers cyber espionage of chemical, defense firms
Attacks against about 50 firms featured e-mails with attachments containing a backdoor.
Hackers targeted about 50 organizations--including chemical and defense companies--in a global wave of cyber espionage attacks this summer, Symantec said in a report released today.
The goal apparently was to steal intellectual property such as design documents, formulas, and manufacturing processes. "The purpose of the attacks appears to be industrial espionage, collecting intellectual property for competitive advantage," according to the report. (PDF)
Meanwhile, French nuclear power group Areva was reportedly targeted in a cyber attack in September.
The wave of espionage attacks on the chemical and other firms started in late July and continued through mid-September, but command and control servers were in use back in April, the Symantec report said. The parties responsible are believed to have launched other targeted attacks against firms in other industries.
"The attackers have changed their targets over time. From late April to early May, the attackers focused on human rights related NGOs. They then moved on to the motor industry in late May," the report said. From June until mid-July no activity was detected. At this point, the current attack campaign against the chemical industry began."
Targets include multiple Fortune 100 companies that do research and development of chemical compounds and develop manufacturing infrastructure for the chemical and advanced materials industry, firms that develop advanced materials for military vehicles, Symantec said.
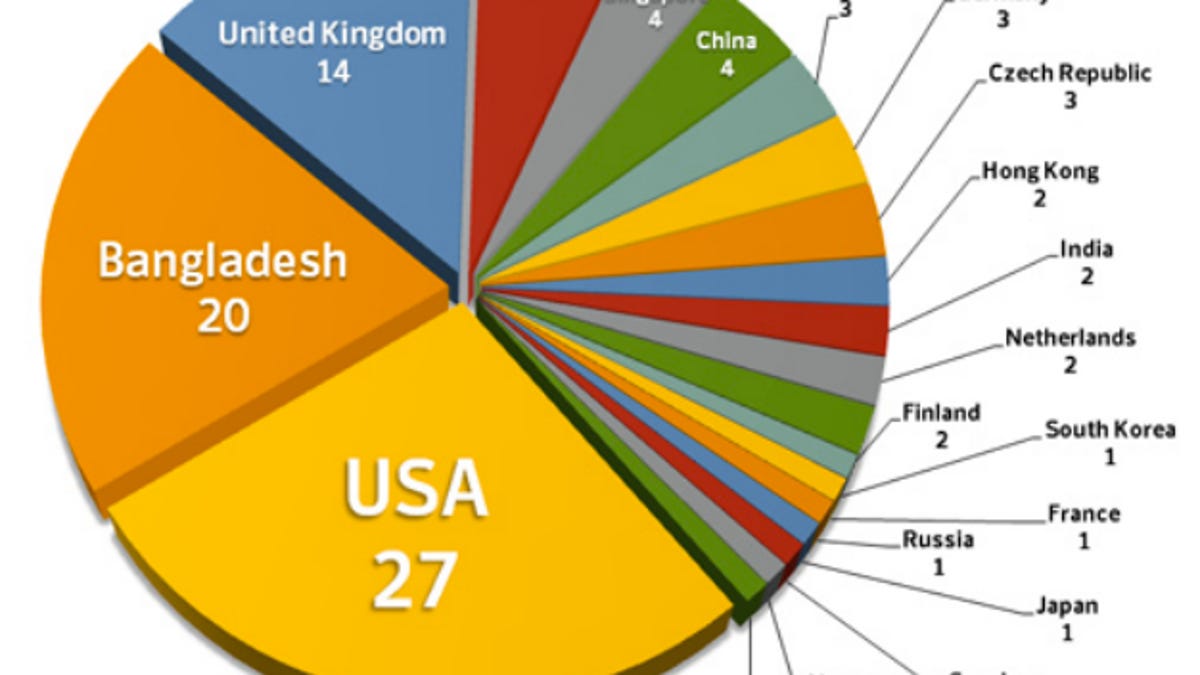
In one two-week period, researchers saw more than 100 unique IP addresses contact a command-and-control server with traffic that appeared to come from an infected machine. The IP addresses were from 52 different ISPs or organizations located in 20 countries, according to the report.
The attackers sent e-mails to employees within the companies, usually pretending to be meeting invitations from existing business partners or to be an important software security update. They were accompanied by an attachment that had a self-extracting executable containing PoisonIvy, a common Trojan that opens a backdoor onto the computer, researchers said.
It's unclear who is behind the attacks, although the report said the attacks were traced back to a virtual private server in the U.S. that was owned by a resident of China's Hebei region who is in his 20s. Researchers have given the man the code name of "Covert Grove" based on a translation of his name.
"We are unable to determine if Covert Grove is the sole attacker or if he has a direct or only indirect role," the report concluded. "Nor are we able to definitively determine if he is hacking these targets on behalf of another party or multiple parties."
Around the same time as the attacks, other hackers were targetings ome of the same chemical companies, sending malicious PDF and DOC files which drop a variant of Backdoor.Sogu, according to the report.
Historically, computer attacks on companies aren't reported publicly. But more reports on attacks on corporations and critical infrastructure providers are becoming more common. In August, McAfee released a report on a cyber-espionage campaigns that stole government secrets, sensitive corporate documents, and other intellectual property for five years from more than 70 public and private organizations in 14 countries.
Google was the first big company in recent years to announce an attack on its network. It announced in early 2010 that hackers, probably from China, had attacked it and a number of other companies in targeted attacks designed to steal information.