Analysis: eHarmony had several password security fails
Security expert says password leak analysis illuminates several no-nos on the part of the dating site.
An analysis of passwords stolen from eHarmony and leaked to the Web recently reveals several problems with the way the dating site handled password encryption and policies, according to a security expert.
The biggest problem clearly was that the passwords, although encrypted and obscured with a hashing algorithm, were not "salted," which would have increased the amount of work password crackers would need to do, writes Mike Kelly, a security analyst at Trustwave SpiderLabs, in a blog post today.
But there were two other less obvious problems. First, the lowercase characters in passwords were converted to uppercase before hashing, Kelly says, writing:
This drastically reduces the time it takes to crack, as there are far less possibilities. Using a full 95 character keyboard, brute forcing an 8 character password gives us 6.6342x1015 possibilities. For eHarmony, this is reduced to 5.13798374 x 1014, due to the loss of the lowercase characters.
And secondly, during resets the passwords were changed to a five-character password using only letters and digits, he said, adding:
During our tests, we reset the password for an eHarmony account several times. Each time, we found that the passwords were reset to a five-character password using only letters and digits. While the password appears to be using uppercase and lowercase letters, we know that the hashes use only uppercase. Bruteforcing five characters, under these circumstances, can be done in less than 10 seconds while utilizing at least one GPU.
eHarmony spokeswoman Becky Teraoka provided this comment to the SpiderLabs post: "The security of our users is of the utmost importance to us. Due to our ongoing investigation and cooperation with law enforcement authorities, we cannot comment on these specific points."
The company, along with LinkedIn and Last.fm, found that user passwords were among approximately 8 million that were posted in two separate lists to hacker sites earlier this month. It appears that while they were hashed, they were not salted, which experts say is a best practice that all e-commerce sites should follow. The companies have notified users, reset passwords and said they are beefing up the security of their password systems.
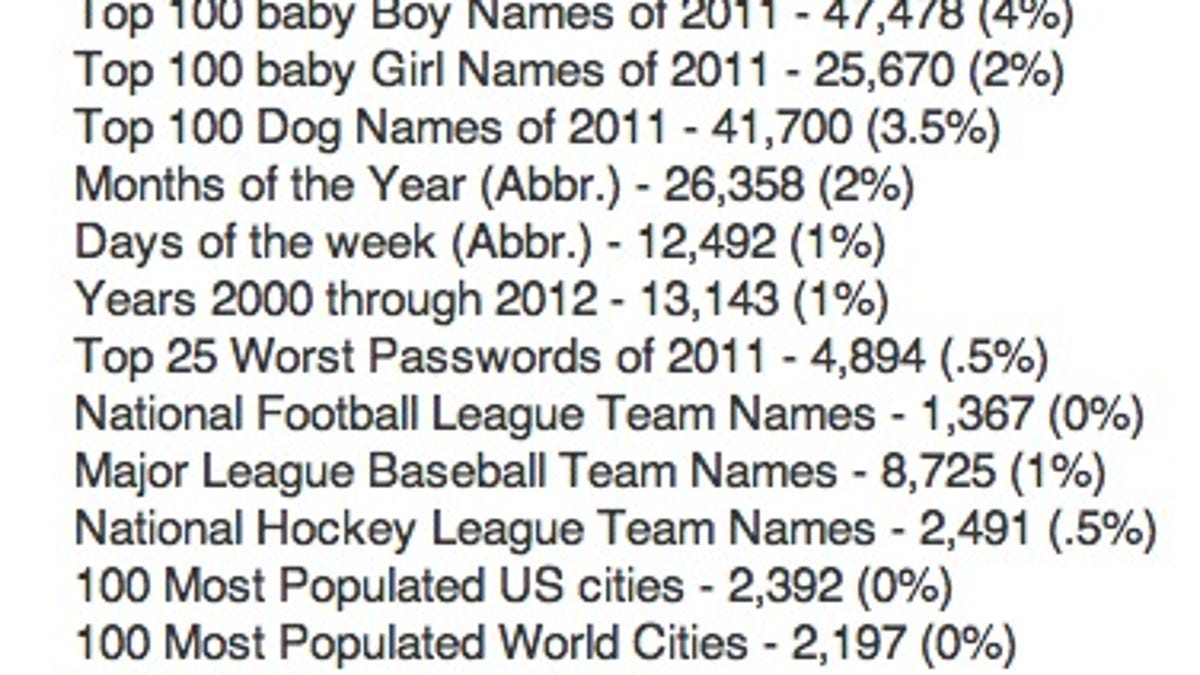
The SpiderLabs analysis uncovered some interesting facts about the types of passwords used on eHarmony. For instance, 99.5 percent of the passwords on the list do not contain a special character, which strengthens the protection, but 57 percent contained letters and numbers. Also, the word "love" was the most commonly occurring password of those that were examined, the analysis found.
Kelly said he couldn't designate what the most common passwords were because no password was seen more than three times on the list. Meanwhile, most of the passwords on the list were seven characters long, followed by six and eight characters in length, he noted.
"The eHarmony dump is just further proof that organizations need to not only store passwords in stronger, salted formats than was previously acceptable, but also need to enforce stronger case-sensitive password policies," the post concludes. "Users, as a whole, still do not understand the need for strong passwords, and will continue to set passwords that meet only the minimum requirements."

