New iOS hack yields in-app freebies
A new exploit gives users free access to digital content within iOS apps, content that normally costs money.
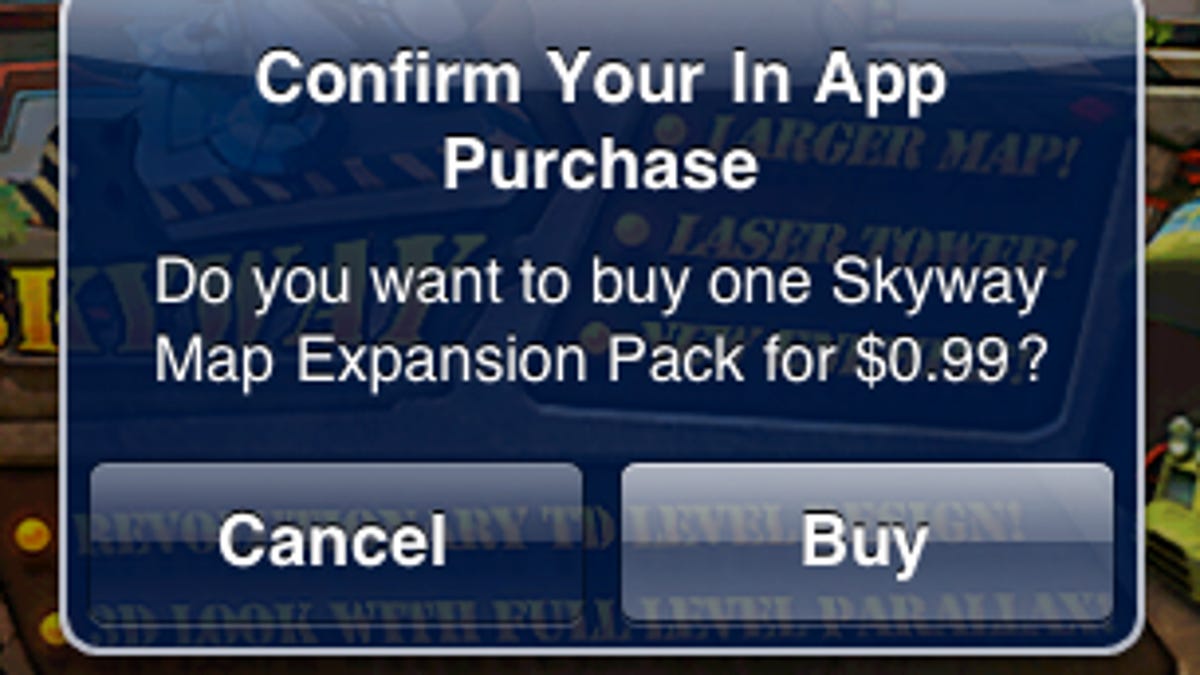
A new exploit aimed at iOS devices enables users to gain free access to paid content within applications, thereby circumventing built-in security measures.
The hack, which was detailed by a Russian programmer and picked up by 9to5mac this morning (via i-ekb.ru), uses a proxy system to send purchase requests to third-party servers where they are validated and sent back to the application as if the transaction had gone through. However before that happens, users need to install special security certificates on their device, as well as be on a Wi-Fi network.
The individual behind the effort has already created a Web site set up for donations to run the proxy servers, which are required to make the trick work.
The loophole goes beyond apps, and covers other types of content that phone home to Apple for verification. That includes Newsstand, the company's digital newspaper service, which typically offers things like newspapers and magazines for free, with in-app purchases to buy subscriptions, or individual issues.
Of note, the demonstration of the hack (which is embedded below) depicts the feature working on a beta version iOS 6, which is due out later this year. Its creators claim it works all the way back to iOS 3, which is when in-app purchasing was first added.
CNET has contacted Apple about the exploit, and will update this post when we hear back.
Apple introduced in-app purchasing in early 2009, and later that year enabled the feature to work inside of free applications. The feature was designed to add an extra revenue stream for developers, as well as simplify the process of publishing apps so that additional paid features could be added even after a piece of software was released. Like app purchases themselves, digital items purchased from within apps carry a revenue split that gives developers 70 percent of the proceeds, while Apple takes the other 30 percent.
Update at 10:30 a.m. PT: Over at CNET sister site ZDNet, Emil Protalinski points to a verification tool developers can enable, which adds a secondary check of the purchase against Apple's own servers:
Your application should perform the additional step of verifying that the receipt you received from Store Kit came from Apple. This is particularly important when your application relies on a separate server to provide subscriptions, services, or downloadable content. Verifying receipts on your server ensures that requests from your application are valid.
Update at 12:40 p.m. PT: The Next Web speaks with Alexey V. Borodin, the creator of the exploit. Borodin says that the way he set it up actually goes around Apple's receipt verification process, suggesting developers with that feature enabled are unsafe from those who are using it. The programmer added that more than 30,000 in-app purchases have been made using the service, which at this time is still up and running.
Video of the exploit in action below:

