New data-stealing Trojan could be Stuxnet version 2.0
Symantec says threat could be precursor to attacks on industrial control systems much like Stuxnet was.
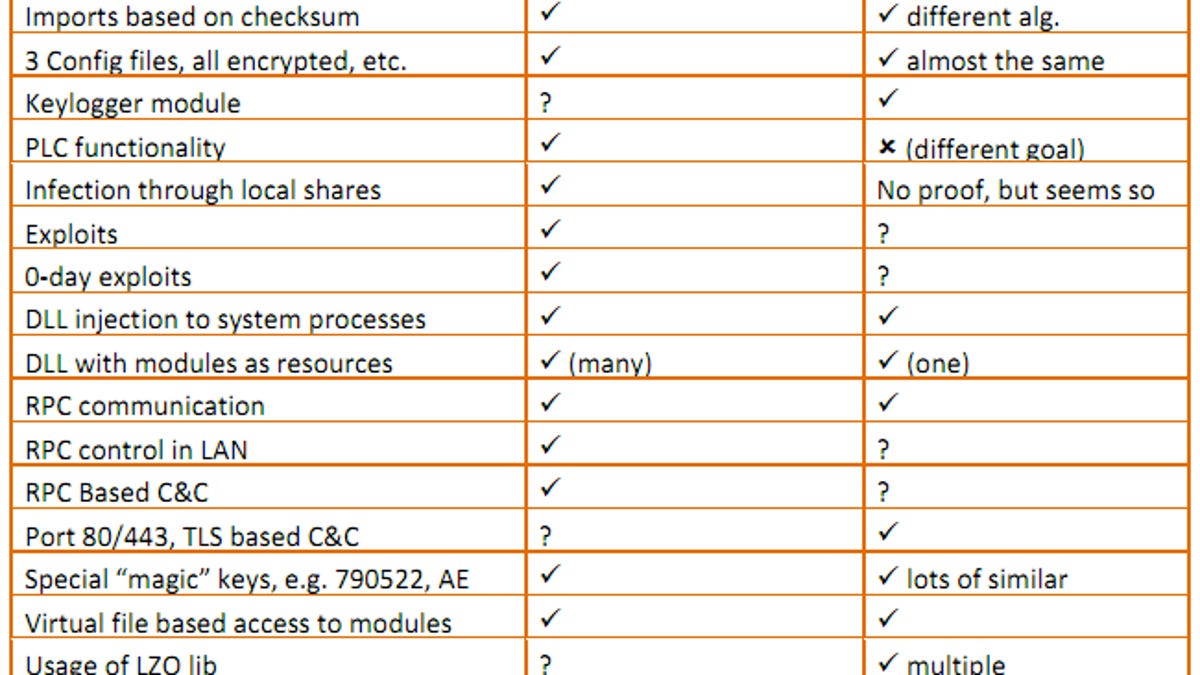
Malware has been discovered on computer systems in Europe that has identical code to the Stuxnet worm and could be the precursor to the next big computer attack on critical infrastructure systems, Symantec said today.
Unlike Stuxnet, which targeted specific Siemens SCADA (supervisory control and data acquisition) software and appeared to have been written to sabotage Iran's nuclear program, the new malware installs a backdoor and is designed to gather information, like design documents, that could be used in future attacks, Symantec said.
The malware, written to run on Windows systems, is dubbed Duqu because it creates file names using the prefix "~DQ." It is a Remote Access Trojan that does not self-replicate but which installs another info-stealer that can record keystrokes and grab other system information, according to Symantec.
"Duqu is essentially the precursor to a future Stuxnet-like attack," Symantec said in a blog post.
Samples of the malware were found on systems of seven or eight companies in Europe, Vikram Thakur, principal security response manager at Symantec, told CNET, but he declined to identify the companies or locations. The code was uncovered by a research lab that has asked to remain unidentified to protect the identity of its customers, he said.
"The first company we saw targeted did not appear to be an industrial control system," he said. "But following samples clearly have a common threat among them. They are industrial control systems, in the process of manufacturing something related to that industry."
It's likely the creators of Stuxnet wrote Duqu, or someone with access to Stuxnet code did, according to Symantec.
"Duqu shares a great deal of code with Stuxnet; however, the payload is completely different," the Symantec post said. "Instead of a payload designed to sabotage an industrial control system, the payload has been replaced with general remote access capabilities. The creators of Duqu had access to the source code of Stuxnet, not just the Stuxnet binaries. The attackers intend to use this capability to gather intelligence from a private entity to aid future attacks on a third party."
It's unclear how a system is initially infected with the Duqu backdoor since the malware does not appear to exploit any vulnerabilities, Thakur said. "We don't know how it initially got onto computers. Could be social engineering, in which someone opened an e-mail with a malicious attachment or clicked on a Web link that led to malware, he said.
"What are they after? We don't know right now. We hope to find out in the next couple of days," Thakur said. "It's gathering basic information about the computer, network, and has a keylogging payload. It's in reconnaissance mode, trying to figure out if there's anything useful in this organization or not."
Two variants of Duqu have been uncovered. The first recording of binary files used in Duqu was September 1, but attacks may have been conducted as early as December 2010, according to Symantec. One of the variants uses a valid digital certificate that appears to have been stolen from a Taiwanese company, similar to the stolen digital certificates used by Stuxnet, researchers said.
Duqu also uses a command-and-control server to download and upload what appear to be JPG files, but which is also used to send out encrypted data. The malware is programmed to automatically remove itself from a system after 36 days, Symantec said. More technical details from Symantec and the unnamed lab that discovered Duqu are in a Symantec report released today. (PDF)
Meanwhile, McAfee released a blog post of its own today on Duqu. That report says Duqu is designed for espionage and targeted attacks against sites such as certificate authorities, which issue digital certificates to authenticate sites and software.
Experts have been worried about Stuxnet copycats and other threats targeting industrial control systems since Stuxnet burst onto the scene last year. The highly sophisticated and multi-pronged threat was the first malware designed to target critical infrastructure systems, like those running energy plants and utilities. Stuxnet exploited previously unreported zero-day holes in Windows to infect specific Siemens software used in industrial control systems and modify programmable logic controllers (PLCs) in order to interfere with external operations of the systems.
Updated 2:07 p.m. PT with more details and McAfee blog post.

