DNC phishing hack was actually a false alarm
Someone set up a fake login page for the Democratic National Committee's voter database.
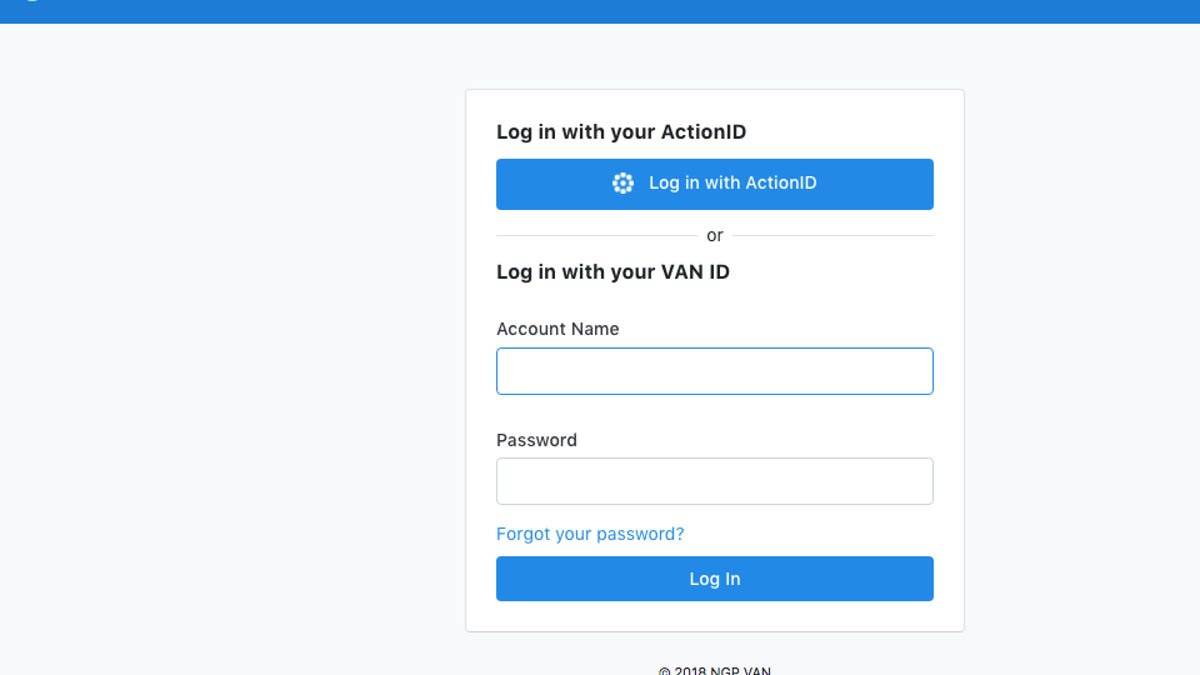
The hacking attempt relied on a bogus login page for VoteBuilder, which hosts the DNC's voter database.
It must have been a bad sense of deja vu for the Democratic National Committee.
A scheme discovered and shut down Tuesday involved someone who seemed to be trying to steal usernames and passwords of Democratic Party officials by way of a fake login page for VoteBuilder, the service that hosts the DNC's voter database.
That was a disturbing echo of an incident during the 2016 US presidential election. At that time, Russian hackers infiltrated the DNC using a similar "spear phishing" method, according to indictments filed in July against 12 Russian agents. And cyberattacks against US electoral systems have only ramped up since. On Monday, for instance, Microsoft said it foiled similar phishing schemes targeting conservative groups.
Tech companies, along with US agencies like the Department of Homeland Security, have increased efforts to protect elections against cyberattacks, which are now coming from nations like China and Iran as well, US National Security Adviser John Bolton said Sunday.
But the trickery uncovered Tuesday seems to have been more benign.
The headquarters of the Democratic National Committee in Washington, DC.
The DNC said late Wednesday that the phishing site was an unauthorized simulation.
"We, along with the partners who reported the site, now believe it was built by a third party as part of a simulated phishing test on VoteBuilder," said Bob Lord, the DNC's chief security officer, in a statement. "The test, which mimicked several attributes of actual attacks on the Democratic party's voter file, was not authorized by the DNC, VoteBuilder nor any of our vendors."
The committee said that the unnamed third party took precautions to ensure that sensitive data was not compromised.
"While we are extremely relieved that this wasn't an attempted intrusion by a foreign adversary, this incident is further proof that we need to continue to be vigilant in light of potential attacks," Lord said.
As it turns out, the phishing simulation came after a request from the Michigan Democratic Party.
"In an abundance of caution, our digital partners ran tests that followed extensive training," the Michigan party's chair, Brandon Dillon, said in a statement. "Despite our misstep and the alarms that were set off, it's most important that all of the security systems in place worked."
The DNC learned about the phishing site Tuesday morning, after security researchers from Lookout, a mobile cybersecurity company, alerted the organization.
Lookout's "Phishing AI," artificial intelligence that automatically picks up on such attack campaigns, discovered the attempt and reported it to DigitalOcean, a cloud provider. The spoof page was almost impossible to distinguish from the original and was taken down within hours, Lookout said in a statement.
"We see no evidence that any sensitive data was stolen, and our initial investigation indicates that we were able to address this threat prior to the attack being launched," DigitalOcean's chief security officer, Josh Feinblum, said in a statement at the time. "We are continuing to partner with the DNC and appropriate law enforcement agencies on this issue."
The DNC contacted the FBI after learning about the hacking attempt. The FBI declined to comment. NGP VAN, the organization that owns VoteBuilder, didn't respond to a request for comment.
CNN reported the attempted hack earlier Wednesday.
First published Aug. 22 at 10:12 a.m. PT
Update at 11:19 a.m.: Added details on how researchers found the spoofed website, along with responses from Lookout and Digital Ocean.
Update Aug. 23 at 5:44 a.m. PT: Added response from the DNC and reworked elements of the story to reflect the DNC's disclosure that the phishing site was a simulation,; Again at 8:49 a.m. PT: Added response from the Michigan Democratic Party.
Security: Stay up-to-date on the latest in breaches, hacks, fixes and all those cybersecurity issues that keep you up at night.
Cambridge Analytica: Everything you need to know about Facebook's data mining scandal.

