Flame virus spread through rogue Microsoft security certificates
The Flame virus that has infected parts of the Middle East took advantage of rogue Microsoft security certificates to deploy its malicious payload.
Microsoft revealed yesterday that the infamous Flame virus gained a foothold by spoofing one of its own security certificates.
Specifically, the virus tapped into rogue certificates for Microsoft's Terminal Server that appeared to be signed by the company and were therefore seen as legitimate. In response, Microsoft has taken several measures, including the release of a Windows patch to fix the security hole in Terminal Server, a feature that allows for remote desktop connections. The company detailed the discovery in a blog posted yesterday.
We have discovered through our analysis that some components of the malware have been signed by certificates that allow software to appear as if it was produced by Microsoft. We identified that an older cryptography algorithm could be exploited and then be used to sign code as if it originated from Microsoft. Specifically, our Terminal Server Licensing Service, which allowed customers to authorize Remote Desktop services in their enterprise, used that older algorithm and provided certificates with the ability to sign code, thus permitting code to be signed as if it came from Microsoft."
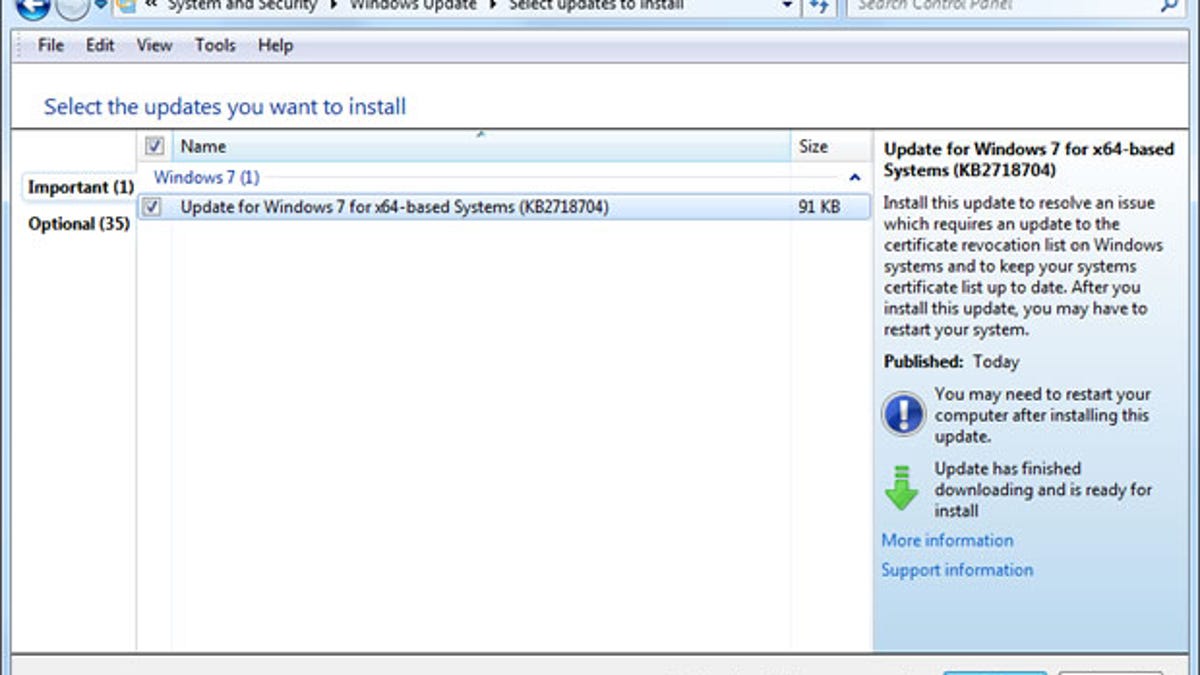
To try to protect its users, Microsoft said it took the following three steps: 1) It issued a Security Advisory on how to block software signed by the unauthorized certificates; 2) It released an update to automatically block the certificates; and 3) It disabled the ability of the Terminal Server Licensing Service to issue certificates that allow code to be signed.
Windows users are urged to install the new KB2718704 patch. If you enabled Automatic Updates, the patch should automatically install. If not, you can open Windows Update on your PC and manually install it.
Flame has aroused great concern among many security experts over its level of sophistication and focus.
Researchers at Kaspersky Lab, who discovered the worm, reported that it can steal data, listen in on audio conversations, and take shots of screen activity.
Affecting Iran and some Middle Eastern countries, Flame is seen by some as a new level of cyberwarfare and is believed to have been developed by a nation state, though other researchers have cautioned against overreacting to the threat.
Since the virus is highly targeted and can be caught by most antivirus programs, the "vast majority of customers are not at risk," according to Microsoft. "That said, our investigation has discovered some techniques used by this malware that could also be leveraged by less sophisticated attackers to launch more widespread attacks," the company added.

