Experts: Google's 'Aurora' hackers still at it years later
Attacks on Google and others three years ago have similarities to new attacks, including use of rare zero-day vulnerabilities.
The hackers behind the cyberespionage attacks on Google and more than 30 other companies three years ago are still going strong and seem to have a steady stream of weapons in their arsenal in the form of rare unpatched vulnerabilities known as zero-days, Symantec researchers said today.
The group has used exploits for four zero-day vulnerabilities in attacks over the past few months against targets across a variety of industries, including energy, aeronautics, and financial, and particularly manufacturers of components sold to defense contractors, the security provider said in a blog post.
"This group is focused on wholesale theft of intellectual property and clearly has the resources, in terms of manpower, funding, and technical skills, required to implement this task," the Symantec white paper (PDF) says.
The campaign from this group, dubbed the "Elderwood Project" by Symantec, has used exploits for previously unknown holes in software including Adobe Flash Player, Internet Explorer, and Microsoft XML Core Services, according to the blog post, which speculated the hackers created at least some of them with the help of stolen source code.
"In order to discover these vulnerabilities, a large undertaking would be required by the attackers to thoroughly reverse-engineer the compiled application," the Symantec post said. "This effort would be substantially reduced if they had access to source code. The group seemingly has an unlimited supply of zero-day vulnerabilities. The vulnerabilities are used as needed, often within close succession of each other if exposure of the currently used vulnerability is imminent."
Symantec researchers believe the recent attacks are linked to the so-called "Aurora" attacks against Google, Adobe and others in late 2009 that exploited a zero-day IE exploit after noting similar code characteristics, timing of attacks, and vulnerabilities used. Google pinpointed China as the source of those attacks. At least eight different zero-day exploits are believed to have been used by the hacker group since the Aurora attack, including that one, they said.Typically, the hackers send targeted "spear phishing" e-mails to specific individuals within a company with a link to a site hosting malware or an attachment that drops a Trojan on the computer when the attachment is opened. The backdoor on the victim's computer then offers a stealth opening for the hackers to steal information from the network.
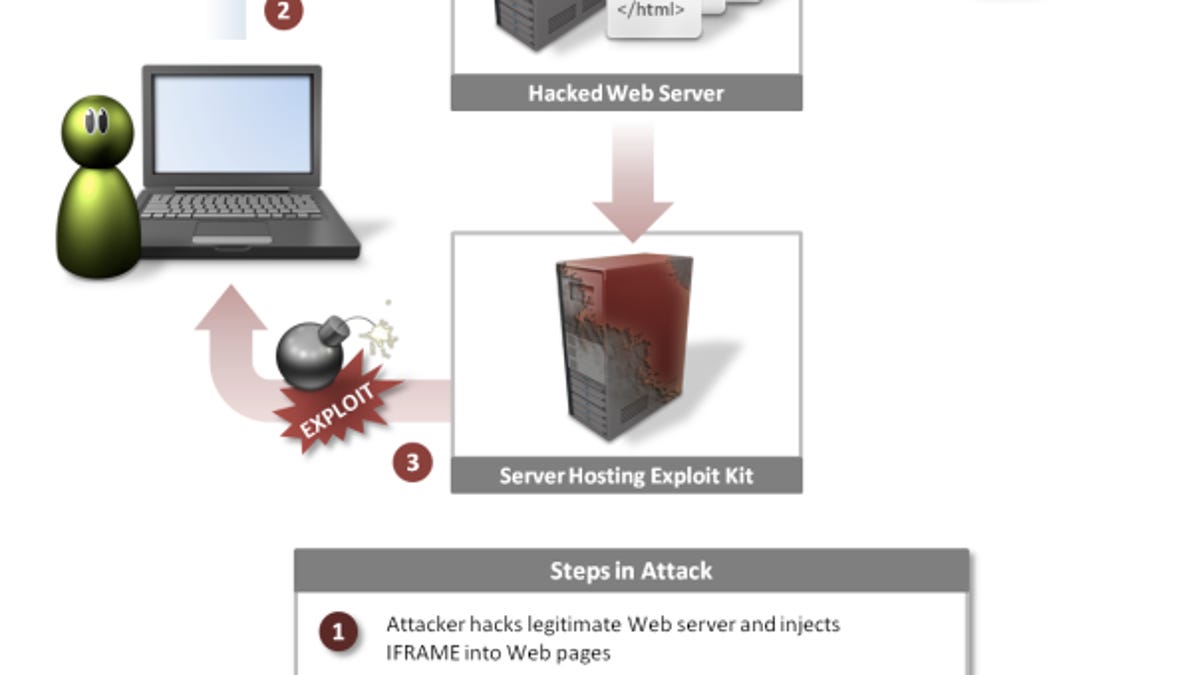
These hackers have been using a new method of infecting victims with malware known as a "watering hole" attack, said Symantec. In this attack, the hackers inject malicious code onto the public Web pages of a site that the targets are known to, or are likely to, visit. Any visitor whose computer is running the software that the hackers have written the exploit for will be compromised. This method has been used by three different zero-day exploits in the last month, according to Symantec.

