New Internet Explorer weakness already exploited in attacks
Researchers say a previously unknown hole in IE has already been used to deliver a trojan in real-world attacks.
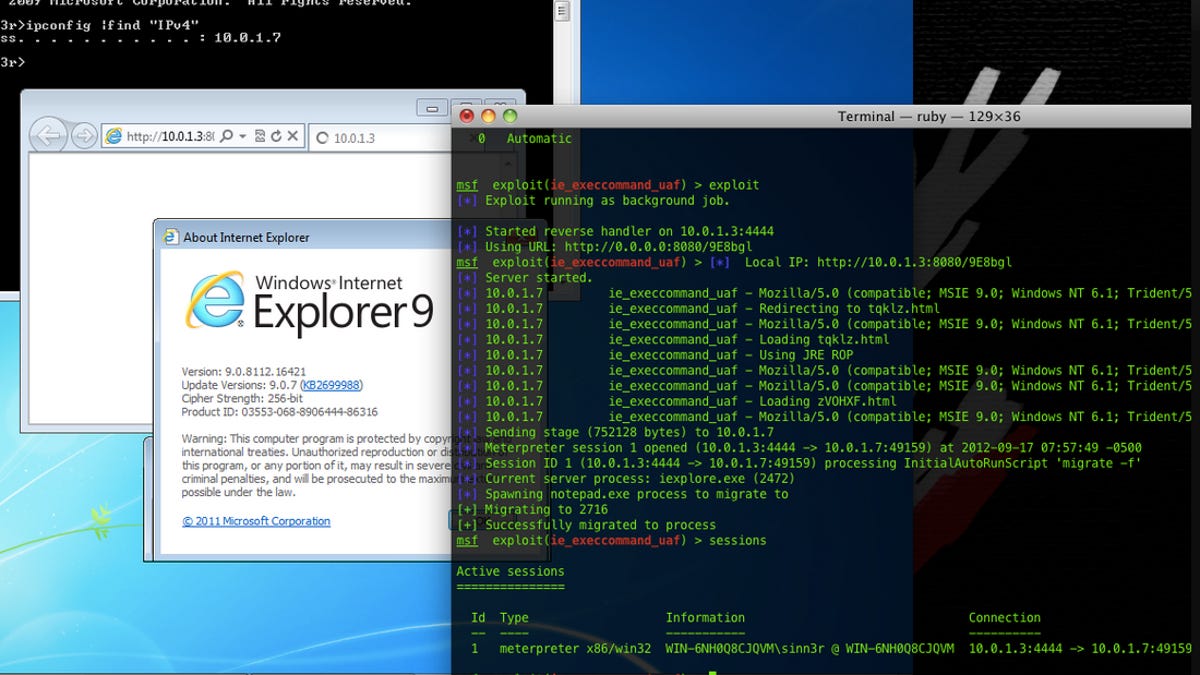
A previously unknown security hole in Internet Explorer 7, 8 and 9 is being actively exploited to deliver a back door trojan known as "Poison Ivy," researchers warned.
Security blogger Eric Romang, who uncovered the vulnerability this weekend, wrote on his blog yesterday:
I can confirm, the zero-day season is really not over yet. Less than three weeks after the discovery of the Java SE 7 0day, aka CVE-2012-4681, potentially used by the Nitro gang in targeted attacks, a potential Microsoft Internet Explorer 7 and 8 zero-day is actually exploited in the wild.Romang found an attack that uses Adobe Flash Player to conduct a "heap spray" technique to bypass ASLR (Address Space Layout Randomization) protection in Windows and allow arbitrary code to be executed on a machine. A "zero-day" vulnerability, by the way, is one that had previously gone undetected.
The attack, which appears to be exploitable on Windows XP, apparently comes from the same parties responsible for a Java zero-day exploit that was uncovered last month, writes Jaime Blasco in a post on the AlienVault Labs blog.
Security experts have already developed a vulnerability-testing tool known as a Metasploit module for IE 7, 8 and 9 on Windows XP, Vista and 7, as explained in a post today on Rapid7's SecurityStreet blog:
Computers can get compromised simply by visiting a malicious website, which gives the attacker the same privileges as the current use. Since Microsoft has not released a patch for this vulnerability yet, Internet users are strongly advised to switch to other browsers, such as Chrome or Firefox, until a security update becomes available. The exploit had already been used by malicious attackers in the wild before it was published in Metasploit. The associated vulnerability puts about 41 percent of Internet users in North America and 32 percent world-wide at risk (source: StatCounter). We have added the zero-day exploit module to Metasploit to give the security community a way to test if their systems are vulnerable and to develop counter-measures.
Microsoft has been looking into the matter and has some advice for protecting against an attack. Here's Yunsun Wee, director of Microsoft Trustworthy Computing, in an e-mail statement:
We're aware of targeted attacks potentially affecting some versions of Internet Explorer.... We have confirmed that Internet Explorer 10 is not affected by this issue. We recommend customers deploy Microsoft's Enhanced Mitigation Experience Toolkit (EMET) 3.0, which provides effective protections without affecting the Web browsing experience. We will continue to investigate this issue and take further actions as appropriate.
Wee didn't say when Microsoft hoped to have a fix for the vulnerability.

