Zeus banking Trojan targets mobile phones too
Researchers uncover version of Windows-targeted malware that tricks people out of mobile numbers to thwart two-factor authentication text message confirmations from banks.
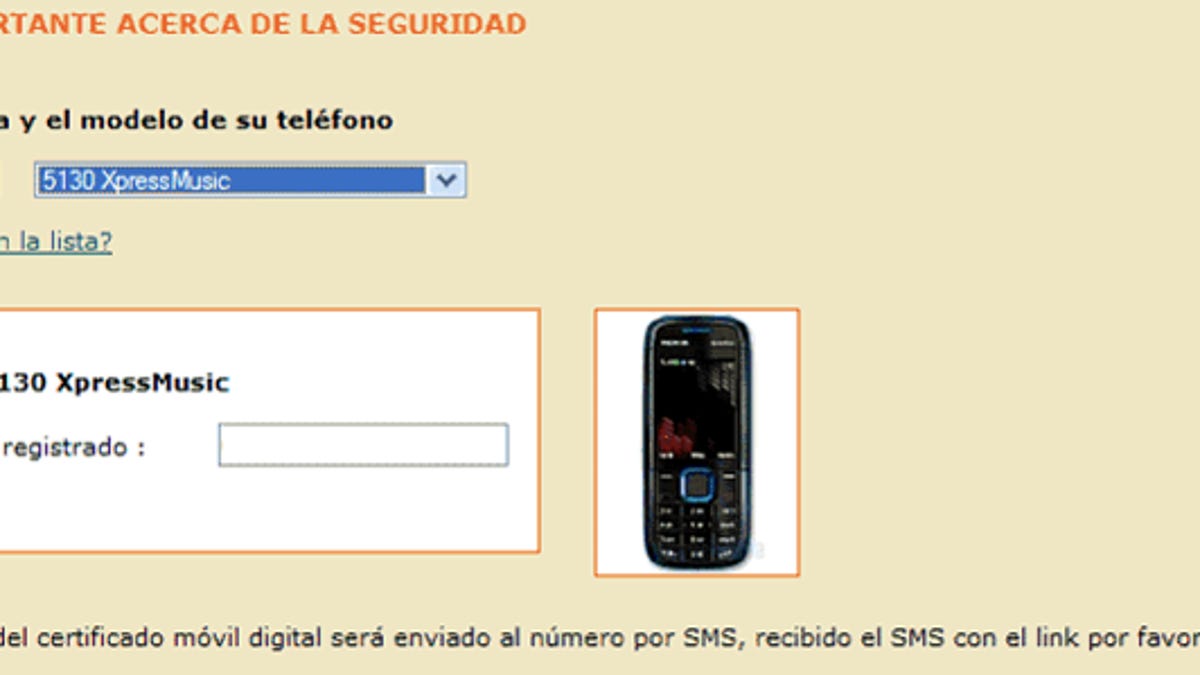
Fortinet said today that it had uncovered new mobile malware dubbed SymbOS/Zitmo, which stands for Zeus in the Mobile, that is most likely designed to intercept confirmation text messages that banks send to customers for online banking. This could allow criminals to thwart banks' two-factor SMS authentication and approve transactions without the victim knowing it.
Zeus typically compromises a computer, either by luring the victim to click on a malicious link in an e-mail or luring the victim to a Web site hosting the malware, so that the bank log-in credentials can be stolen. In this attack, the malware displays a pop-up box in the browser that prompts victims to supply their mobile numbers and phone model. It then uses that information to send a text message to the victim that contains a link to a version of the malware written for that mobile platform, Fortinet said.
"This malicious package is still under investigation, but given the context, it is logical to believe it is aimed at defeating SMS-based two-factor authentication that most banks implement today to confirm transfers of funds initiated online by their end users, and that currently impedes the plunging of infected users' online accounts by Zeus masters," the Fortinet blog post says. "(Note: although it was possible before, with man-in-the-middle attacks, it required the victim to initiate a financial transfer in the first place)."
The malware monitors all incoming text messages and installs a backdoor for attackers to use to control it, according to Fortinet.
The mobile attack is explained in three separate posts on the S21sec blog.
"We are working with mobile carriers to help them to detect infected devices," the S21sec blog says. "Mobile carriers are the key actors in this incident, just because they are the only ones that can detect which devices are infected and block all the connections to/from the mobile C&C."
Meanwhile, phone users should monitor their bank accounts and mobile SMS charges, the company said.

