Study: DDoS attacks threaten ISP infrastructure
Arbor Networks finds that DDoS attack sizes doubled last year and were more diverse in nature, taxing the IT security resources at most Internet carriers.
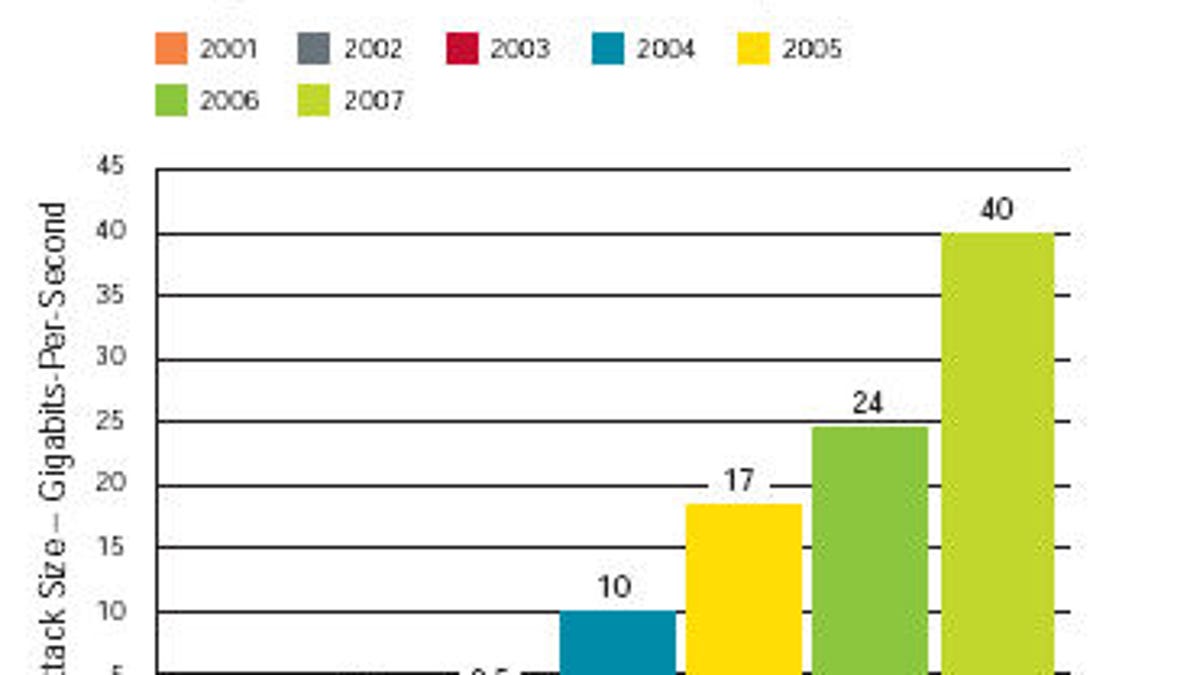
Internet service providers now spend most of their IT security resources detecting and mitigating distributed denial-of-service attacks, concludes a report from Arbor Networks.
The fourth edition of the Worldwide Infrastructure Security Report, released Tuesday, was based on how 70 lead security engineers responded to 90 questions. As in the previous three reports, ISPs reported attacks where their networks were overloaded with packets, what's called a distributed denial-of-service (DDoS) attack. However, this year, the ISPs indicated the attacks were not only larger in size but that most of them were stretching the upper limits of their security resources in order to deal with such attacks.
Rob Malan, founder and chief technology officer of Arbor Networks, said the DDoS attacks seen this year broke the 40-gigabit barrier, nearly double the volume of last year's attacks. He warned that if next year's attacks again double in size, "most carriers will be unable to deal with those attacks."
In assessing the attacks, Arbor Networks found "brute force," a catch-all term, was the dominant method used. The security firm looked at traditional means of DDoS--syn flood, udp flood--as well as anything else that artificially created network congestion. Malan told CNET News that despite the massive size, the attacks themselves demonstrated "little sophistication" and were simply "trying to overwhelm network bandwidth."
One consequence of this method was that upstream providers of the targets were increasingly being affected. "If an attacker takes out capacity of (the upstream) routers you're (also) starving the target," he said. Malan said attackers were also using reflective attacks, which use different pieces of DNS structure to redirect traffic away from a target.
While flood-based attacks represented 42 percent of the attacks reported, followed by protocol exhaustion-based at 24 percent, Arbor Networks also saw a sharp increase this year in application-based attacks, which accounted for 17 percent of the attacks.
Malan explained that with application-based attacks, bot-infected computers worldwide make connections to a targeted site, then "use an application protocol to deliver a perfectly valid request, not a vulnerability, not something that an IDS or other type of firewall would necessarily flag." For example, a botnet might instruct its zombie computers worldwide to do a back-end query off a database. "By itself it's not bad, but if you have multiple such requests, then you tie up the application--in this case database--resources on the back end," he said.
The report does contain some good news. Arbor Networks found detection and mitigation of these attacks to be increasing as well. Fifteen percent of the respondents said, on average, they can mitigate an attack within 10 minutes of detection. However, 30 percent said mitigation still takes them over an hour.
But finding the criminals responsible for these attacks is not a high priority. Arbor Networks found that ISPs have little time to involve law enforcement. "It's hard on carriers," said Malan. "They get paid on traffic, not to do forensic analysis. So it's hard from their perspective to make the economics work."

