Face.com plugs Facebook, Twitter hijacking hole
Researcher works with companies to close hole that allowed anyone to hijack KLIK user's accounts on Facebook and Twitter.
A hole in the Face.com mobile app KLIK has been closed after a researcher discovered that it could be used to hijack Facebook and Twitter accounts.
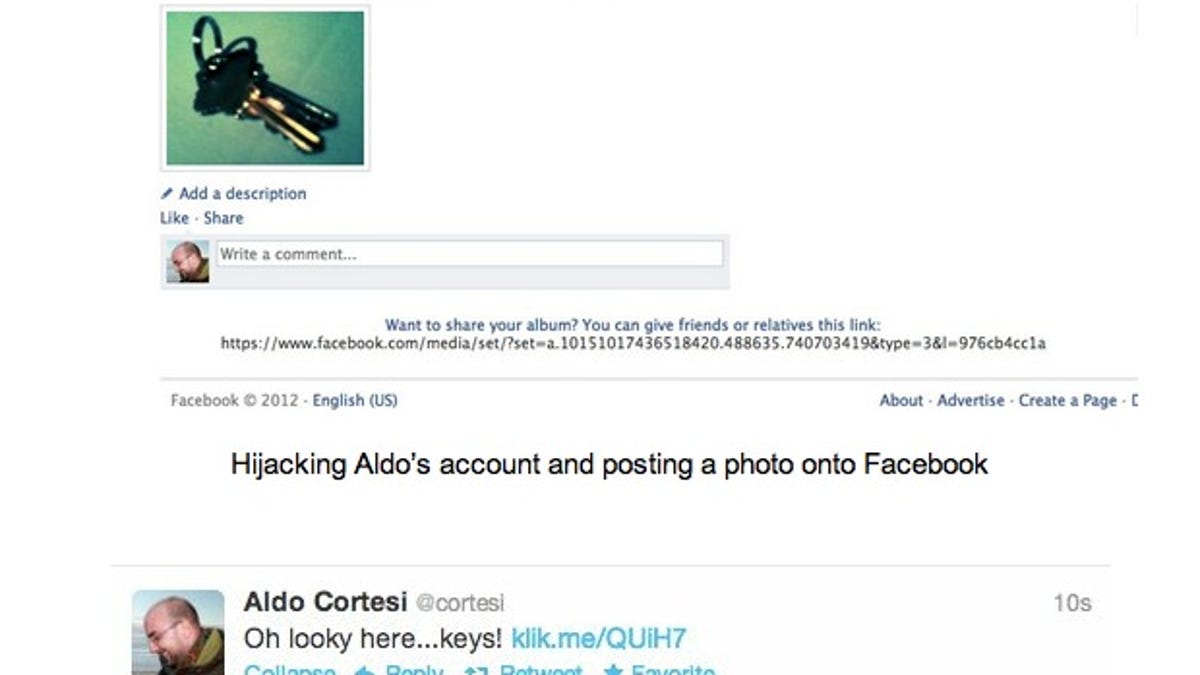
KLIK lets people tag faces in photos using Facebook, which recently acquired Israel-based Face.com. But Ashkan Soltani, a privacy and security researcher, found that it also allowed anyone to hijack a KLIK user's accounts on Facebook and Twitter to get access to photos that were private.
"The above attack not only allows access to non-public photos, but also lets the attacker potentially manipulate the Face.com app to automatically 'recognize' anyone walking down the street (i.e just hijack Lady Gaga's and get her ~11 million friends' 'face prints')," Soltani wrote in a blog post yesterday.
"In addition to accessing a potentially private data (i.e., if they had their photos, friends lists, or tweets set to 'private'), the vuln allowed the attacker to hijack the account and post status updates / Tweets as that user," he wrote. "Since KLIK relies on Facebook connect, that means anyone that has used the app was vulnerable."
The problem arose because Face.com was storing Facebook and Twitter OAUTH authorization tokens on servers insecurely. Soltani said he waited to disclose the problem publicly until after it was resolved.
