DDoS attacks spread to vulnerable IPv6 Internet
The next-gen Internet, still immature, is now a pathway for Net attacks, a study finds. Also, ideology has become the primary reason for DDoS attacks.
The idyllic byways of the next-generation IPv6 Internet now suffer an affliction previously limited to the mainstream IPv4 Internet: distributed denial-of-service attacks.
And worse, the still-immature IPv6 network is being caught with its pants down when it comes to repelling the DDoS attacks. That's the conclusion of Arbor Networks' latest annual study on the Internet's operational security, released today.
"This is a significant milestone in the arms race between attackers and defenders," Arbor Networks said. "We believe that the scope and prevalence of IPv6 DDoS attacks will gradually increase over time as IPv6 is more widely deployed."
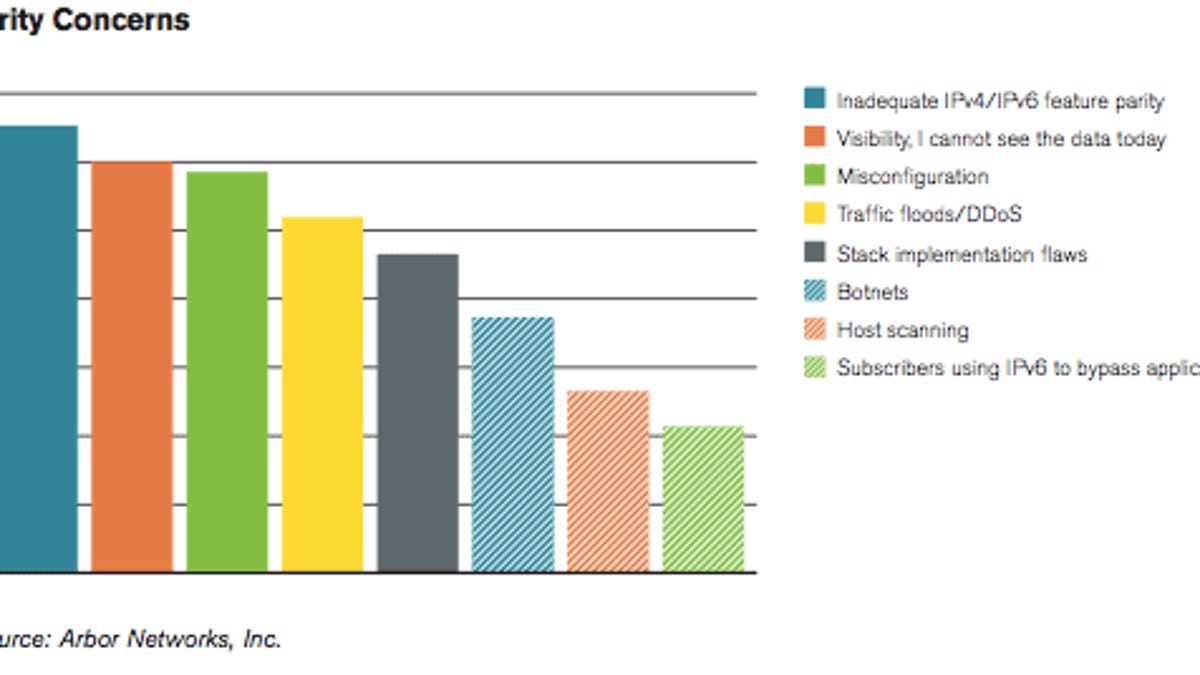
For the moment, the volume is still relatively small--only 4 percent of survey respondents reported seeing IPv6 DDoS attacks--but that's a worrisome harbinger.
DDoS attacks use a swarm of computers to swamp a target machine on the Internet with traffic so it's unusable. Such attacks sometimes are launched from botnets of compromised computers for criminal reasons--but now the top cause is ideology such as that evident in Anonymous' coordinated protest attacks.
DDoS attacks send traffic to a particular Internet address, and today the vast majority of those addresses are handled by Internet Protocol version 4, or IPv4. IPv6, which vastly increases the number of possible addresses to deal with the fact that IPv4 is running out of them, is gradually becoming a reality as those with servers and network gear invest in the new network.
IPv6 isn't the main route for attacks, since it's still a relative backwater, but two problems make IPv6 particularly vulnerable. First, with the relatively immature network infrastructure, many network operators don't have the ability to scrutinize network traffic well enough to distinguish DDoS attacks from benign traffic. Second, gateways that link IPv4 and IPv6 must store lots of "state" information about the network traffic they handle, and that essentially makes them more brittle.
Arbor forecasts greater protections, though. "Twenty percent of respondents indicated that they have no plans to mitigate IPv6 DDoS attacks. We suspect that priorities within these organizations may evolve rapidly as IPv6 network traffic becomes more prevalent," Arbor said.
Investments in countermeasures are expensive--but so are DDoS attacks.
Survey respondents reported varying costs of dealing with a DDos attack: about $1,300 or $8,000 in two cases, $250,000 or $300,000 in two others, and $1 million to $1.5 million in two others. And of course there are other costs, for example when a business or government can't get work done or sell products.
Powerful attacks the "new normal"
The study, a global survey of network operators such as Internet service providers, also finds that DDoS attacks have become more powerful, more sophisticated, and more routine. And the leading cause: ideological attacks such as launched by Anonymous after MegaUpload arrests.
"Ideology was the most common motivating factor for DDoS attacks in 2011, followed by a desire to vandalize," Arbor Networks said. The finding is "one of the single most important data points in this year's report, with major implications in terms of threat assessment, situational awareness, and continuity of operations for network operators, governmental bodies, law enforcement agencies, and end customers alike."
Although the top bandwidth of an attack decreased from 2010's 100 gigabits per second to 2011's 60 gigabits per second, it's increasingly common to see attacks that send tremendous traffic, Arbor said.
"During the survey period, respondents reported a significant increase in the prevalence of flood-based DDoS attacks in the 10Gbps range. This represents the 'mainstreaming' of large flood-based DDoS attacks, and indicates that network operators must be prepared to withstand and mitigate large flood attacks on a routine basis," the report said.
Growing DDoS sophistication
In earlier years, distributed denial-of-service attacks traveled by lower-level network protocols such as TCP (Transmission Control Protocol), which is used to ensure that data is successfully delivered across a network.
Now, though, attacks are moving to higher-level services such as HTTP (Hypertext Transfer Protocol), which is used to send Web pages to browsers; DNS (Domain Name Service) for translating text-based Internet addresses into their numeric equivalents; SMTP (Simple Mail Transfer Protocol) for sending e-mail; HTTPS for encrypted Web page communications; and voice over Internet Protocol (VOIP).
That's driven in part by new attack software. "HTTP GET and HTTP POST [two HTTP commands] were the most common application-layer DDoS attack vectors, more sophisticated mechanisms such as Slowloris, LOIC, Apache Killer, SIP call-control floods, SlowPost and HOIC are increasingly prevalent," Arbor found.

